

What is Malware Attack and How to Prevent It?
Attackers find every way to exploit businesses and individuals through a variety of cyber-attack techniques. Malware attack is one of them. Of course, it is not a new kind of attack technique, it has existed for a long time now.
The history of malware attacks can be traced back to 1982 when it was defined as a simple unwanted software that used to spread through floppy disks to Apple II systems. Though it didn’t cause any harm to computers, it did lead to unwanted intrusion.
Since then, malware has evolved a lot and has become quite a major cyber threat. For all cybersecurity professionals, beginners, and experts, as well as every individual using connected devices, it is important to be aware of malware attacks and their prevention techniques.
In this article, we will thoroughly understand the types of malware, how they can affect our systems, how we can detect and eliminate them, and more. So, read along.
What is Malware?
Malware, short for malicious software, refers to software programs that are intentionally designed to cause damage to computers, networks, servers, or any kind of digital device. While regular software serves a specific purpose for the users, malware works with a malicious intent often without the user’s knowledge or consent.
They can do a lot of damage including stealing or corrupting important files, locking devices, monitoring user activity, etc.
Do you know, 300,000+ new malware types are detected daily and each day AV-TEST Institute registers new malware and PUPs with over 60 million new strains found in 2024? (Source: AVG)
How Malware Affects Systems and Users?
Malware is intentionally designed to harm computers, networks, and other digital assets. They are of different types and depending upon their goal, they can affect users differently.
Some common harmful actions they perform are:
- Data theft. Malware can steal your sensitive information including login credentials or other financial data
- System damage. It can corrupt system files or crash your device’s operating systems to make it inoperable
- Ransomware attacks encrypt data. Ransomware is a type of malware that encrypts files and even lock devices. The data or devices are unlocked only after you pay the ransom money for decryption.
- Spy. Yes, certain malware is highly advanced and can be used to monitor your activities and collect your data, and transmit it to attackers. Malware can also get access to the camera and mic on your device without your knowledge and spy on you. Sounds scary, right?
- Create a botnet. This means attackers turn your infected devices into bots and exploit the resources such as your computational power and network to carry out large-scale DDoS attacks.
- Unwanted advertisements. Malware called adware can also bombard you with huge amounts of intrusive advertisements leading to further malware infections, adult content, or other harmful or malicious sites.
You will really not want to be infected with malware for the damage to peace of mind and digital assets it will cause to you. But how does it infect your systems?
These are some of the most common malware infecting users and businesses worldwide:
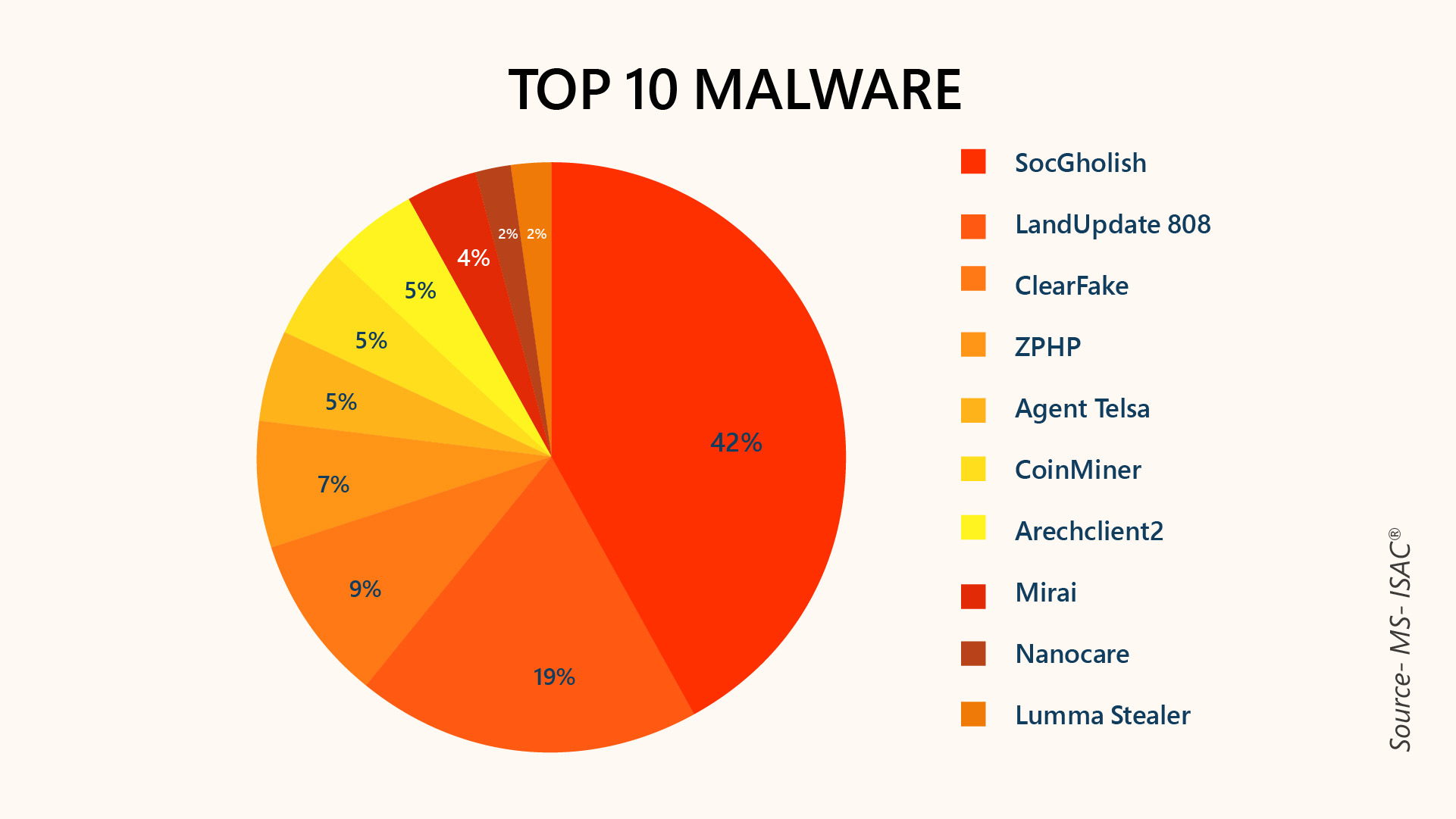
How Does Malware Get into Your System?
Well, there can be several reasons for malware infection. They can be spread through various channels such as:
- By opening emails infected with malicious attachments. It is the most common way of malware attack triggering malware installation
- By visiting compromised or infectious websites or clicking on malicious links that automatically download and install malware
- Through removal devices like USB drives or external hard drives infected with malware
- Some attackers also employ techniques like exploiting security vulnerabilities and flaws in software which gives them access to inject malware
- Downloading and installing pirated software often comes bundled with malware
- Malicious advertisements on genuine websites also lead to malware attacks as they can redirect users to malicious sites and trigger automatic downloads.
These malwares can be of various types and designed for various purposes as described in the next section.
Do you know, that the best cybersecurity certifications like the ones offered by USCSI® provide a detailed curriculum on underlying concepts of malware and their prevention strategies? So, earning one can significantly enhance your knowledge of this cybersecurity concept.
Common Types of Malwares
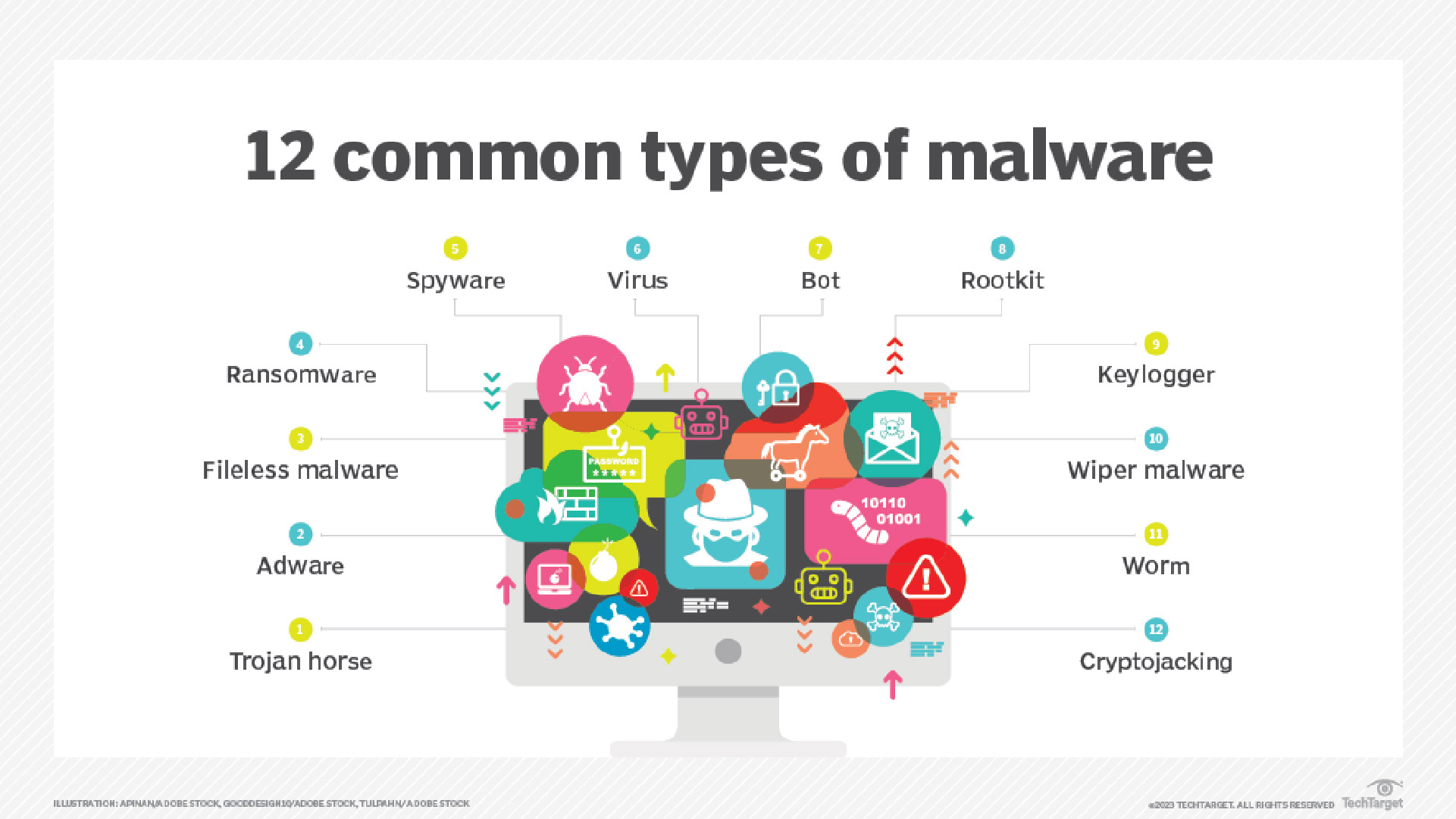
Malware comes in many forms with each having distinct characteristics and functionalities. Here are some common types of them:
- Viruses
They are often attached to executable files and spread when the infected file is run. They cause huge damage to the systems by replicating themselves.
- Worms
They are different from viruses as they can spread independently over networks without any host file. They exploit vulnerabilities to propagate rapidly.
- Trojans
Like the mythological Trojan horse, these Trojan malwares also disguise themselves as genuine software and trick users into installing them. After installation, they perform malicious activities like stealing data or opening backdoors for attackers.
- Ransomware
It refers to the type of malware that encrypts systems or user files and demands ransomware in return for decryption. It leads to operational downtime, reputational damage, and financial loss.
- Spyware
This type of malware is used to spy on users. They secretly monitor user activities and collect different types of data including their financial information, browsing history, keystrokes, login credentials, etc., and transmit them to attackers.
- Adware
Adware bombards users with unwanted advertisements. These advertisements often lead to further malware infections.
- Rootkits
They hide other malware that are present in the system which makes it difficult to identify and remove the dangerous malware.
- Keyloggers
These are other common malware types that record your every keystroke and capture sensitive information such as passwords and credit card details.
How To Detect Malware?
So now, how do you know if your computer or network is infected by malware and how do you detect them? Of course, this can be difficult as malware operates secretly without your knowledge, but thankfully, there are ways common signs suggesting the infection such as:
- Slow computer performance
- Unusual error messages
- Missing or corrupted files
- Blue screen of death
- Increased unwanted internet activity
- Change in file names and sizes
- Popups and advertisements
- Anti-malware software scans
- Programs opening and shutting automatically, etc.
All these are signs of your systems being infected with malware. So, the important question – how do you remove them? Let’s see.
How To Make the System Malware-Free?
You need to be very careful to remove malware and avoid any further damage.
Here are a few ways cybersecurity professionals and individuals use to remove malicious software:
- Using anti-malware software. Running a full system scan will help detect and remove various types of malwares
- Anti-malware tools are specialized software that can target specific types of malwares and remove them effectively
- Manually remove malware. But this requires technical expertise and caution to avoid further damage
- Restoring the system to previous restore points before the infection happened can also help remove malware in some cases
- You can also consider reinstalling the operating systems or performing a complete system format/restore. However, this should be done in severe cases when no other options are left, because it will leave you with a clean system and all-important files deleted.
There are many tools that offer antimalware solutions that organizations and individuals can consider such as:
- Bitdefender GravityZone
- CISCO Secure Endpoint
- ESET Protect
- F-Secure Total
- Kaspersky Premium
- Sophos Intercept X
- Webroot Managed Detection and Response, and more.
These tools can effectively help you detect and prevent malware attacks in real-time. But we all know prevention is better than cure and therefore we must try to avoid ways to inject malware.
How To Prevent Malware Infection?
There can be chances that the antimalware tool might not work properly and the malware can remain undetected. Therefore, the best way to remain protected from them is by preventing malware infection.
Here’s what you can do:
- Always install and use software from trusted organizations, official websites, and sources. Avoid using pirated software
- Rely on reputable antivirus software that can detect and block malware entering your systems
- Always keep your software, operating systems, applications, and browsers updated with the latest security patches to eliminate vulnerabilities
- Never click links on unsolicited and suspicious emails. Do not open their attachments.
- Be careful when accessing sensitive information from public Wi-Fi networks because they are often not so secured
- Using a firewall can help block unauthorized access to your computer
- Keep yourself and your dear ones updated about evolving malware threats and ways to avoid malware injection
- Using pop-up blockers can help block malicious advertisements in browsers and prevent accidental clicks on malicious content.
You need to be a responsible user to avoid this increasing cyber threat. Be vigilant, and follow these steps to keep your systems, networks, and data safe.
You must also be aware that only malware is not dangerous for your systems. There are several other similar programs such as Grayware, Browser hijackers, tracking cookies, RATs, etc. We will discuss in detail about them in later posts. So, keep watching this space and subscribe to our newsletter for regular updates and interesting information to keep yourself protected.
Malware attacks are evolving and growing, but they are not the end!
Once you are aware of different types of malwares and how they can be detected, you can easily identify and prevent intrusion into your system. So, implement the preventive measures we discussed and enhance your organization’s overall security and defense. Following these essential steps won’t just protect you from financial losses, but keep your data and reputation safe and secure.





