

What is Data Loss Prevention - Understanding DLP Tools and Trends
With data breaches becoming omnipresent, guarding cyber walls with a robust defense mechanism has become quintessential. But this does not always work. Cybersecurity technology becoming a costly affair worldwide, it has garnered much attention over the years as the velocity of malicious social engineering attacks grew humungous.
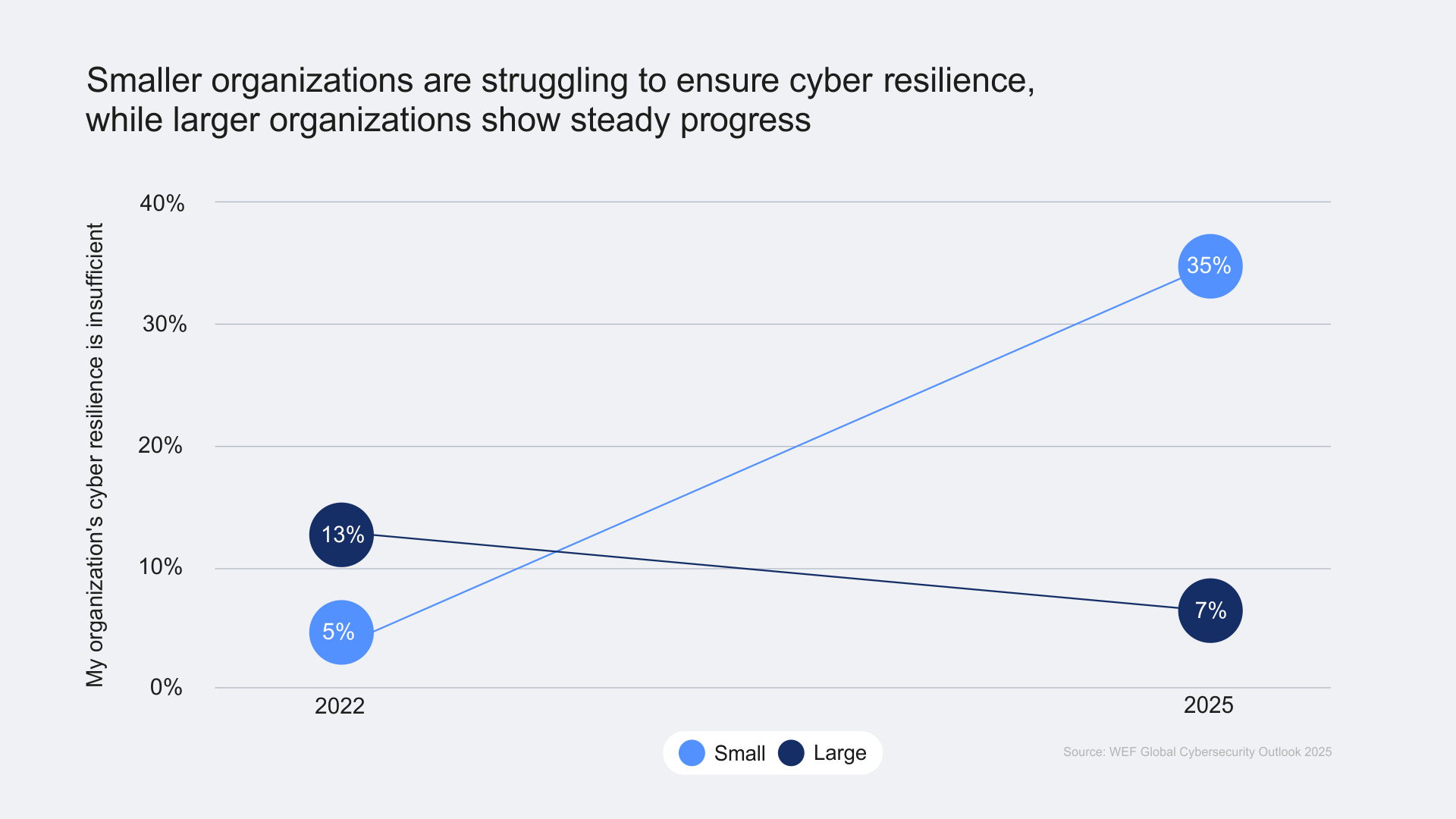

This builds up greater threat concerns for the larger organizations as well. The cost of cybercrime is expected to reach USD 10.5 trillion annually by 2025; indicating a significant rise in cyberattacks; representing a 15% yearly increase in cybercrime costs globally- mastering security nuances is critical for safe survival (Cybersecurity Ventures).
Understanding the loopholes and the stringent way to guard cyberspace is a must when planning a robust security setup. Before you begin thinking deeply, let us explore data loss prevention and related aspects in detail.
Cybersecurity Vulnerabilities Anticipated in 2025
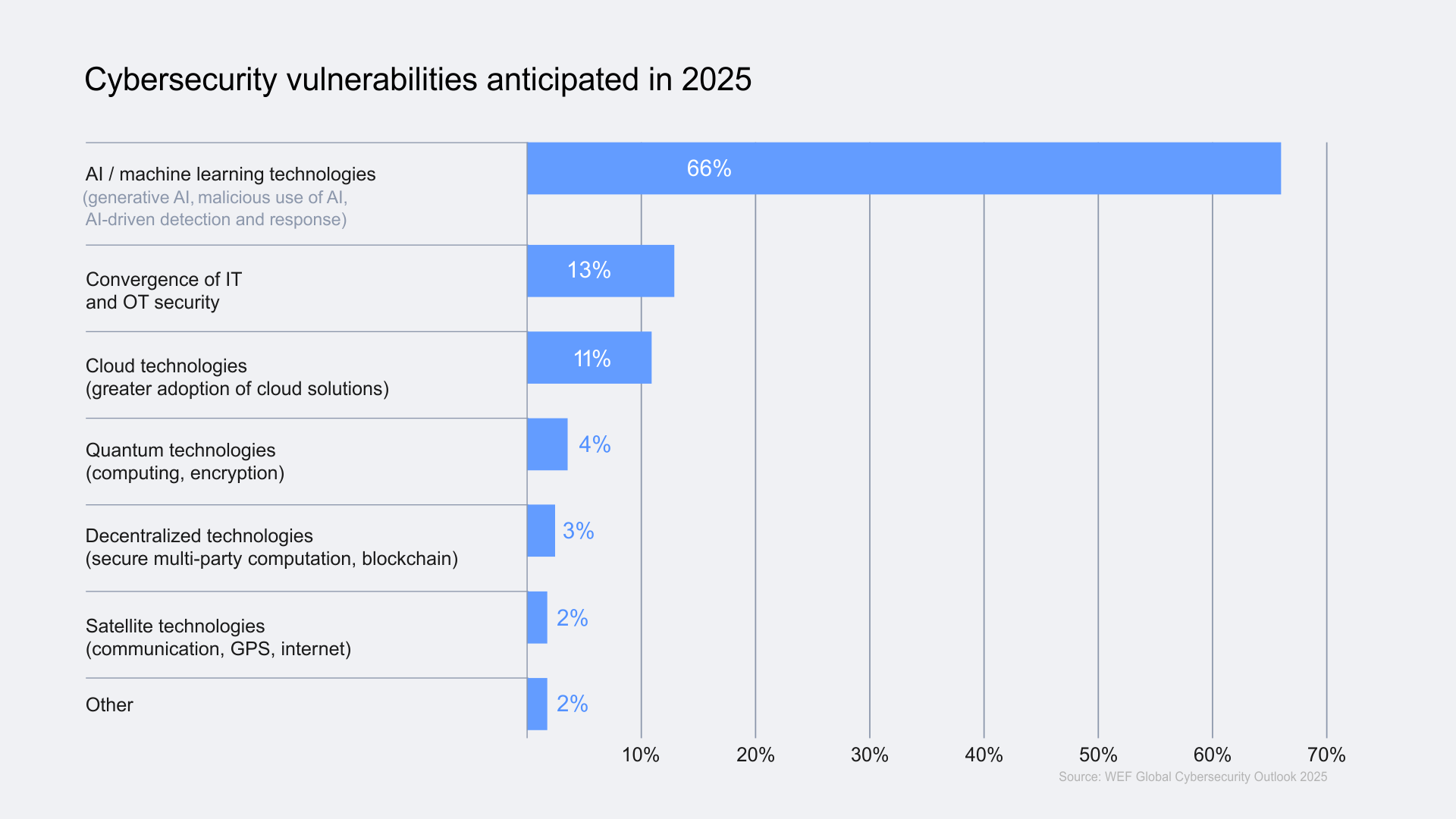
While 66% of organizations expect AI to have the most significant impact on cybersecurity in the year to come. Only 37% report having processes in place to assess the security of AI tools before deployment (WEF GCO 2025). This reveals the gap between the recognition of AI-driven cybersecurity risks and the rapid implementation of AI without the necessary security safeguards to ensure cyber resilience.
Data Loss- Types and Causes
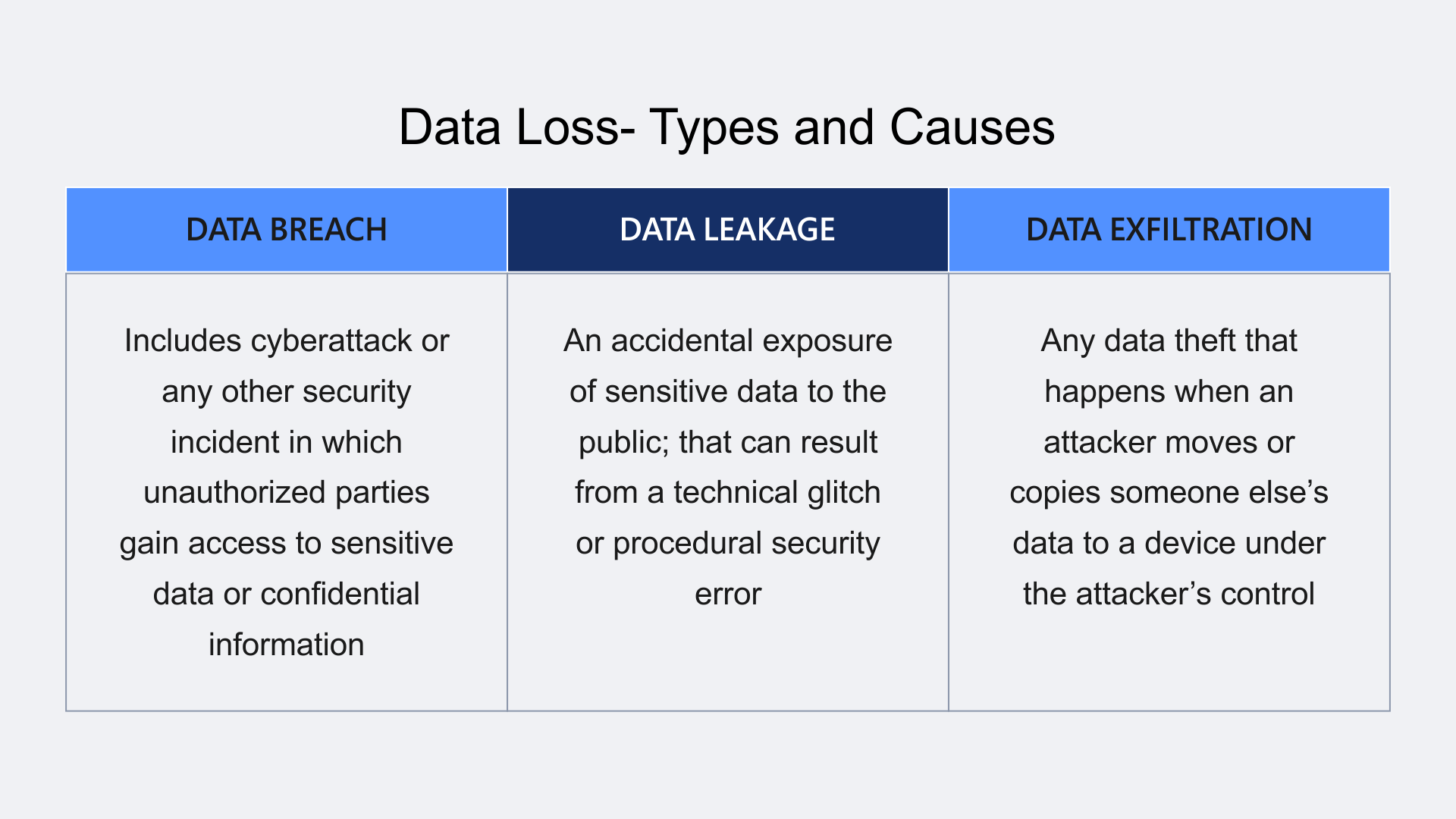
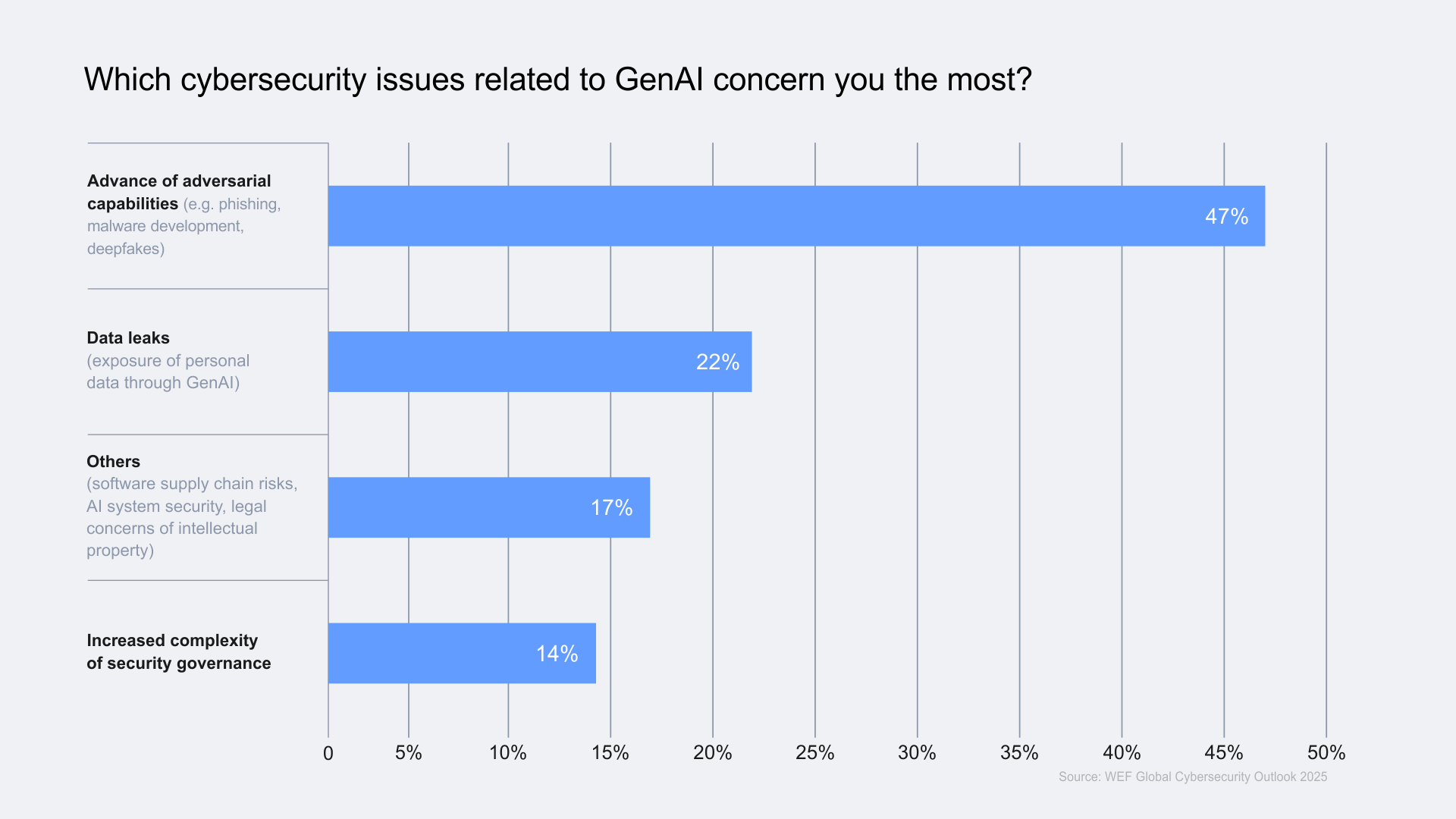
Note that all data exfiltration requires a data leak or a data breach, but not all data leaks or data breaches lead to data exfiltration. Continuing with the threat landscape numbers, the following reflects upon the respondents’ core issues concerning the tech giants as the GenAI expanse goes beyond bounds.
Understanding Data Loss Prevention (DLP)
DLP in cybersecurity refers to the strategy that targets the prevention of unauthorized access, usage, or transmission of sensitive data by actively monitoring data at rest, in motion, and use; detecting potential data breaches, and blocking actions that could lead to data loss. It is a power-packed security solution that identifies and helps prevent the unsafe sharing; or usage of sensitive information.
DLP- Importance
- Data discovery and classification
- Monitoring and enforcement
- Encryption and access controls
- Prevention of data loss
- Data protection
- Reduced insider threats
- Cost savings
- Compliance assurance and reporting
DLP- Core Components
- Data encryption- A vital component of DLP, data encryption works by converting sensitive data into an unreadable format (ciphertext) that can be accessed or decrypted only by authorized users with the correct decryption key.
- Access controls and permissions- User permissions define who within your business can access, edit, or share data and under what circumstances. These systems are typically managed using role-based access controls (RBAC), which limit access to sensitive data based on an employee’s role or specific responsibilities; thereby reducing the risk of unauthorized access.
- Employee awareness and training- Providing employees with regular training via best cybersecurity specialist certifications, is crucial to help them recognize potential threats, handle sensitive data responsibly, and follow established security procedures. This enables them to understand the trends in data loss prevention and stay proactive.
- Secure backup and recovery- Creating duplicate copies of critical data and storing them in separate, secure locations, whether on-premises, in the cloud, or both are essential parts of backup and smooth recovery.
DLP- Action Plan
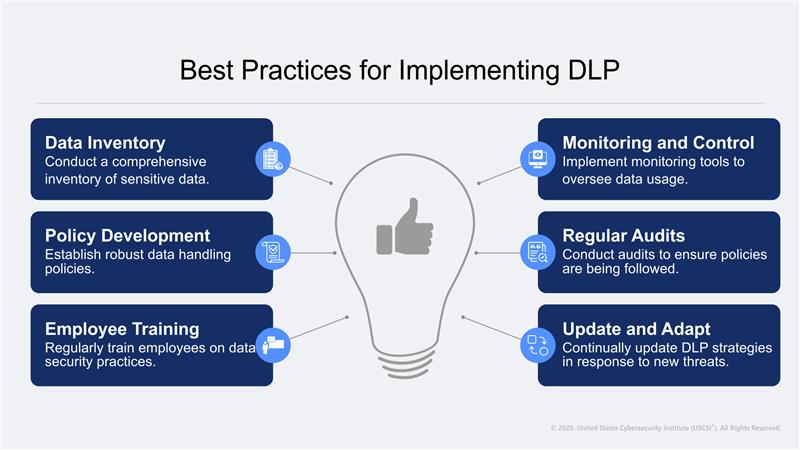
Utilizing these remedial measures; you are sure to build a thriving safety net for cyberspace. As it shows, leading at the top is employee training- this forms the nuclei of the entire security process. Cybersecurity professionals and aspirants can ramp up their skills by learning cybersecurity strategies that are imparted as part of the curriculum of most of the trusted cybersecurity certifications.
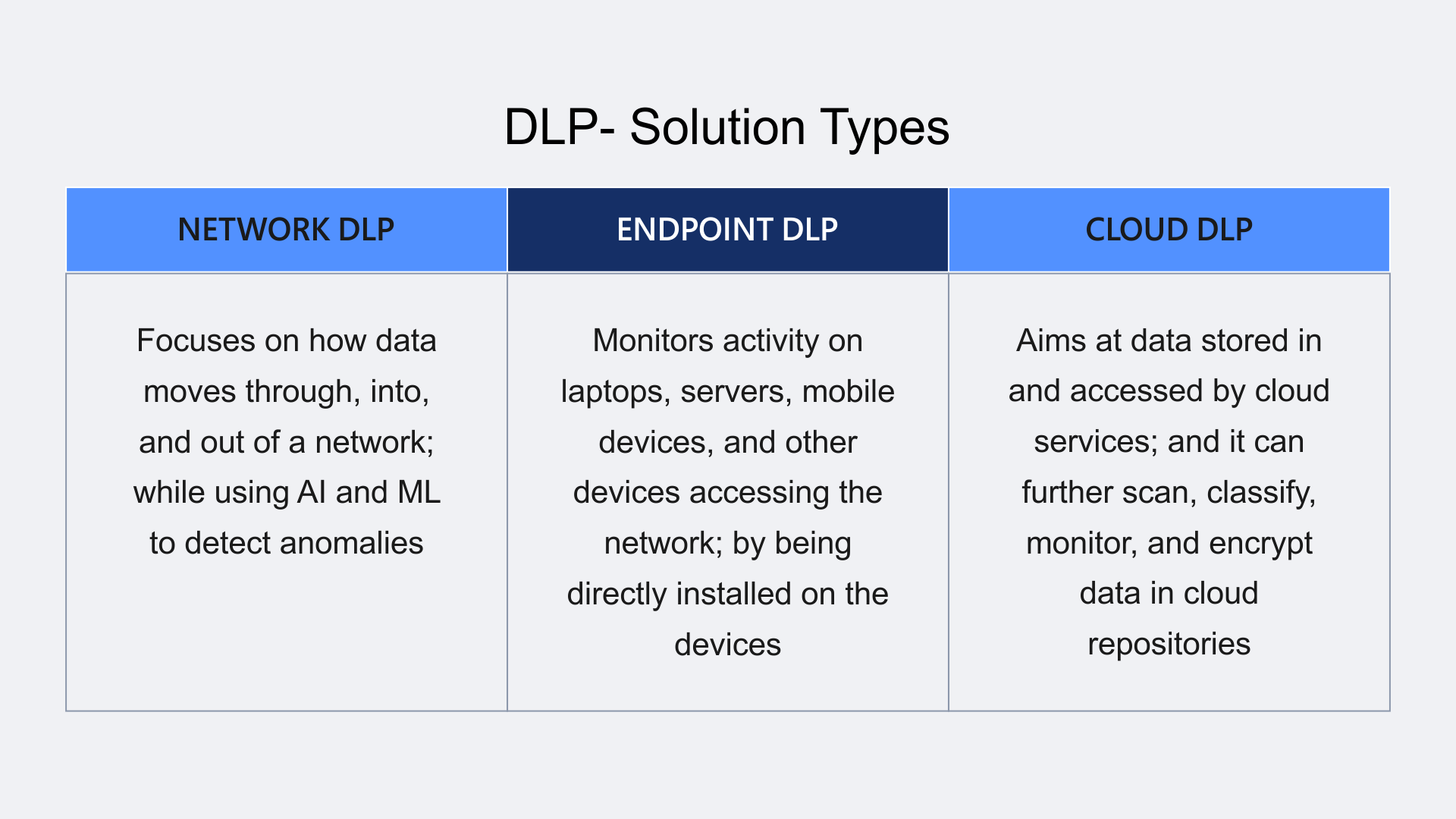
DLP- Solution Types
DLP- Top Tools
- Digital Guardian DLP by Fortra- Supports managed services and offers excellent customer support and on-demand training
- Forcepoint DLP- Provides broader highly effective monitoring and analysis capabilities while consuming minimal resources on endpoints
- Palo Alto Network Enterprise DLP- Designed to accommodate mobile and hybrid workforces and SaaS application usage and allows quick and easy setup
- Proofpoint Enterprise DLP- Highly customizable rules and dictionaries and is relatively easy to implement compared to other DLP products
- Symantec DLP by Broadcom- Offers greater UI flexibility and ease of usage; along with fast data discovery and strong detection of policy violations reported
- Trellix Data Security (formerly McAfee)- Multiple users consider the data protection methods highly effective and appreciate the management console’s UI
- Zscaler Data Protection- Widely fuss-free deployment and requires no on-premises applications or other hardware; that leaves it to be highly scalable
DLP- Key Trends
- Hybrid multi-cloud environments- Many organizations now store data on-premises and in multiple clouds, possibly even in multiple countries; that adds flexibility and cost savings big time.
- Generative AI- As the graph reflected in the previous sections, GenAI will contribute to data leaks and cyberattacks to about 17% by 2027 (Gartner).
- Stringent regulation- The EU AI Act and CCPA draft rules on AI are the strictest data privacy and protection rules to date.
- Mobile workforce- Gartner predicts that “by the end of 2026, the democratization of technology, digitization, and automation of work will increase the total available market of fully remote and hybrid workers to 64% of all employees.
- Shadow IT and Shadow data- Organizations are also dealing with an increase in shadow data—that is, data in the enterprise network that the IT department does not know about or manage. The proliferation of shadow data is a major contributor to data breaches.
Choosing the Right DLP Matters- Quick Tips
- Scope of monitoring and protection across different channels
- Presence of local agents for endpoint protection
- Analytical capabilities to detect and respond to threats
- Integration with existing systems
- Cost-effectiveness and ease of implementation
Role of Cybersecurity Specialists in Data Loss Prevention
As a seasoned certified cybersecurity professional, you are elemental in performing the most hygienic and strategic Data Loss Prevention strategies to safeguard the sensitive information of your business or employer. The cybersecurity skills and capabilities that you bring to the table are quintessential for the long-term survival of any organization. Get your hands on the best cybersecurity certifications as you plan to build a thriving cybersecurity career with your dream job in place.




