

Continuous Threat Exposure Management: Benefits and Processes
Threats to organizations are no longer as simple and predictable as they used to be a few years ago. Today, advanced technologies like artificial intelligence, machine learning, deepfakes, and more have made threats almost unpredictable and highly sophisticated and have become very difficult to detect.
The number and cost of cybercrimes are in no way expected to decrease, and in such a scenario, the traditional security measures and strategies that often rely on point-in-time assessments and reactive responses might not be efficient in providing adequate security to modern cyber-attacks. This is where Continuous Threat Exposure Management (CTEM) comes into play.
This read will help you understand what this security strategy is, how it works, its notable advantages, and how you can implement it within your organization for enhanced security.
What is Continuous Threat Exposure Management (CTEM)?
A recent report by Gartner predicted that 45% of organizations will be affected in some way or other because of supply chain attacks. Not just that, the cost of cybercrimes is expected to hit $23 trillion by 2027 (source: U.S. Deputy National Security Advisor).
Seeing these increasing threats and cost, we can say reactive approaches to cyber-attacks are no longer a wiser option. Therefore, CTEM offers a more proactive approach to this problem.
Continuous Threat Exposure Management (CTEM) is not just a buzzword now. It refers to the new strategic process in which organizations perceive and manage their security posture. It is a systematic and ongoing process that helps organizations identify, prioritize, and mitigate threats and vulnerabilities spread across their entire attack surface.
Instead of just relying on periodical security audits and assessments, the CTEM techniques require organizations to perform continuous monitoring and analysis and take necessary actions to improve their security state and keep them protected against evolving and emerging cyber threats.
Need for Continuous Threat Exposure Management (CTEM)
Now, the question arises: Is there a need for CTEM, and what does it entail? Well, CTEM is an important step in the organization’s cyber-resilience and vulnerability management program.
Here is what CTEM additionally offers in comparison to traditional vulnerability management processes:
- Continuous Threat Monitoring
CTEM, as the name suggests, involves continuous monitoring of an organization’s overall attack surface, from their devices to data and networks to applications. Regular monitoring of threats on premises, cloud environments, or end points gives cybersecurity professionals clear visibility and faster detection of all kinds of threats.
- Threat Prioritization Based on Risk
It is also important to note that all the vulnerabilities are not serious. While some vulnerabilities can be eliminated with security patch updates, some may require serious attention. The level of severity is different in all cases. CTEM helps with the prioritization of remediation efforts of such vulnerabilities based on their risk and severity. It can take into account factors like how easily a vulnerability can be exploited, what its impact could be, and how critical it would be to organizations if the assets are affected.
- Automated Analysis and Correlation
The advanced CTEM techniques use automation and machine learning to analyze large amounts of data and find anomalies. This is essentially beneficial in detecting complex attack patterns that otherwise would go unnoticed in traditional methods.
- Proactively Remove Vulnerabilities
CTEM doesn’t only help with threat identification, but it can also offer proactive solutions to threats in real time, including patching, configuring changes, and adjusting security controls. This minimizes the window of opportunity for attackers and prevents costly damage.
Understanding the Five Stages of CTEM
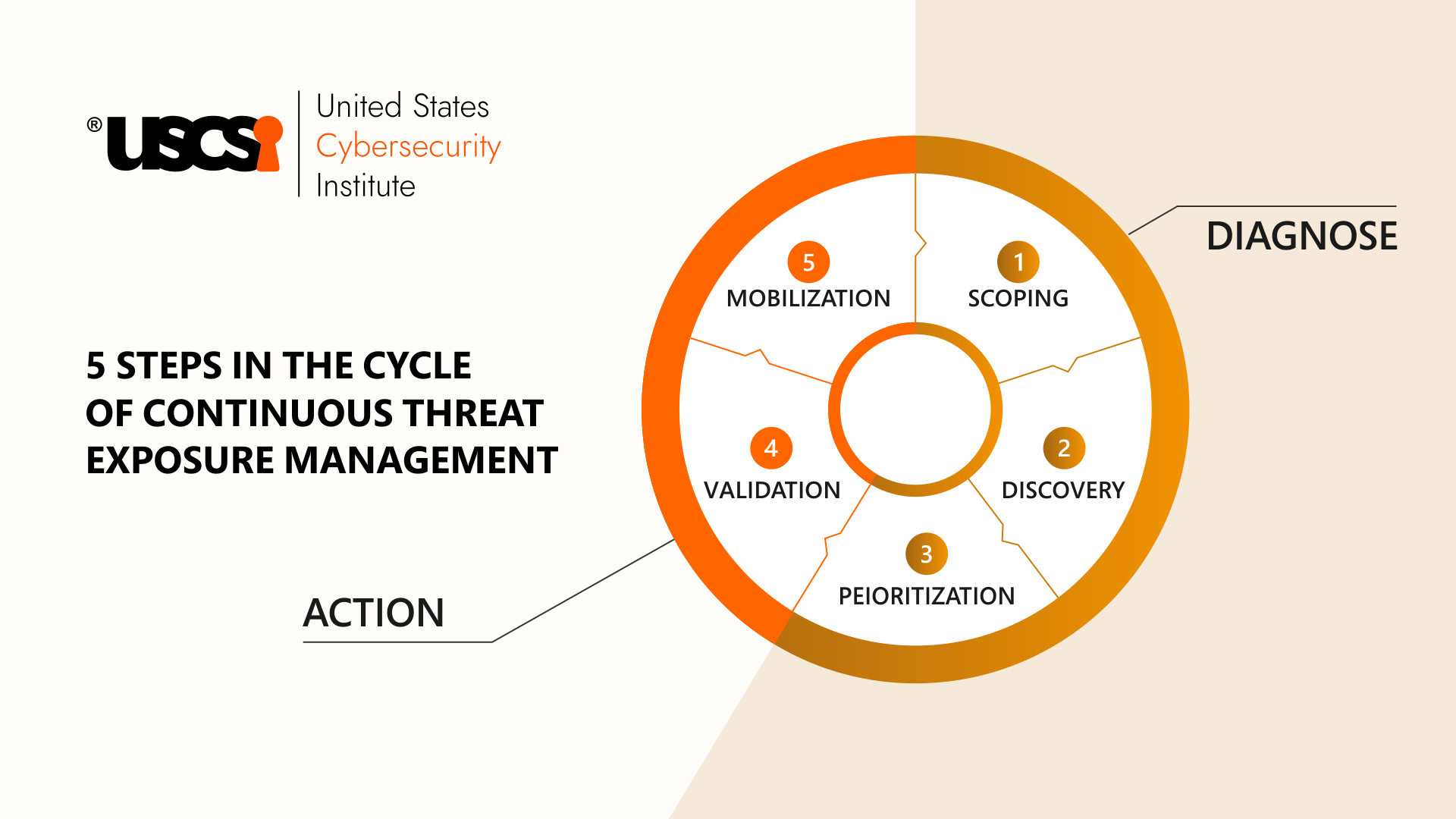
- Scoping
The first step of effective Continuous Threat Exposure Management (CTEM) is defining the scope of the program where organizations need to assess the impact of vulnerabilities and exposures. They might need to consider external attack surfaces as well that can serve as an entry point for attackers.
- Discovery
This stage involves the identification and mapping of an organization’s every attack surface, such as their applications, networks, devices, etc. This provides them with the clear visibility needed for effective threat and vulnerability management.
- Prioritization
In this step, organizations need to prioritize the vulnerabilities and exposures based on their assessment in previous steps for elimination. They can prioritize the vulnerabilities based on their criticality and exploitability.
- Validation
Before cybersecurity professionals start eliminating vulnerabilities, they should validate them first. This can be done with a variety of techniques like vulnerability scanning, penetration testing, or other security assessment methods.
- Mobilization
Finally, the last step is to take necessary actions to eliminate the identified threats and vulnerabilities. This step includes processes like patching software, configuring changes, and implementing new security controls.
Benefits of Continuous Threat Exposure Management
Organizations can implement CTEM and enjoy several benefits in enhancing their security. Here are some advantages of CTEM to consider for implementing this technique:
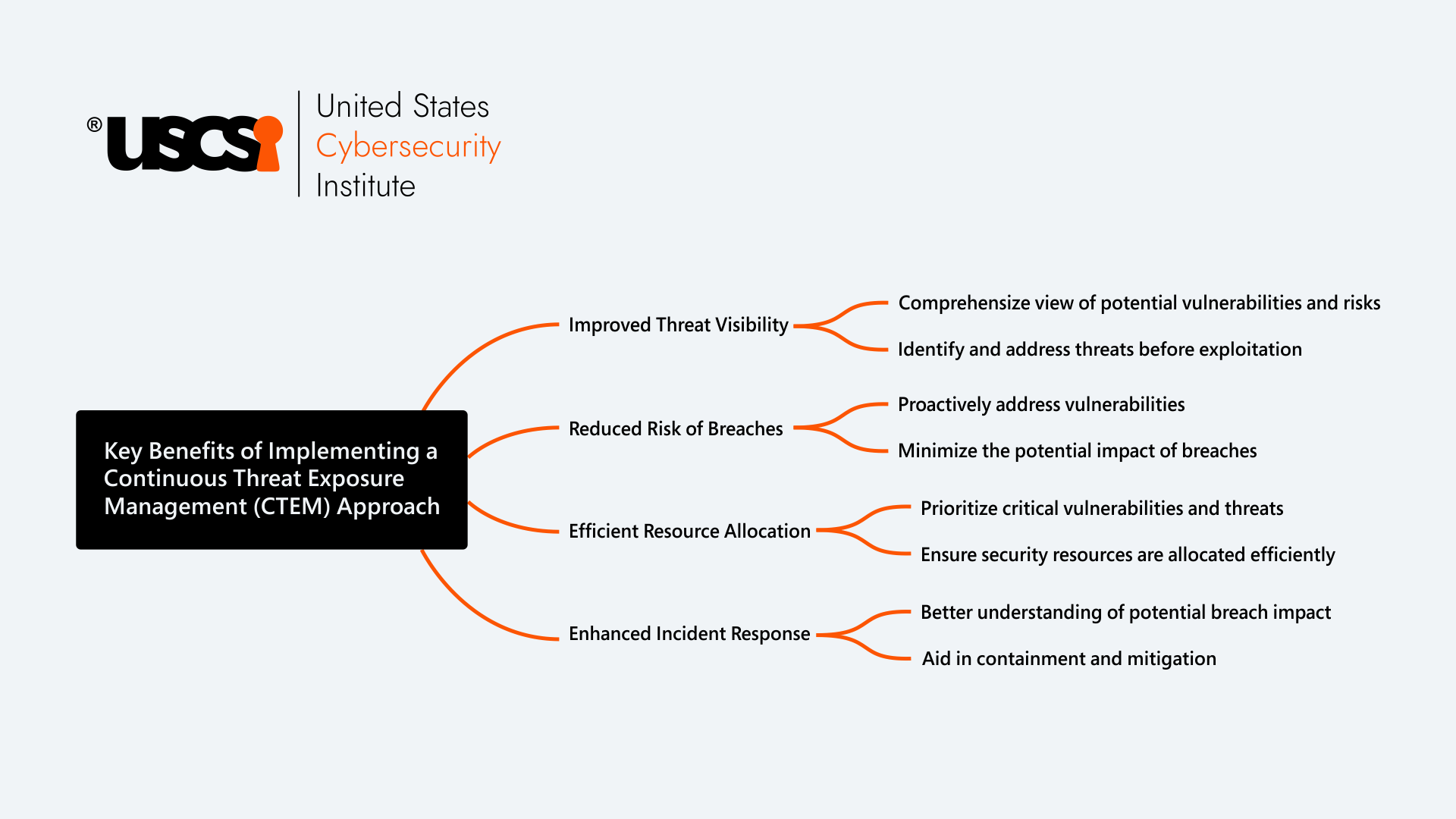
- Lower risk of data breaches – Data breaches can cost $4.88 million on average, and effectively implementing CTEM can assist organizations in reducing the risk of data breaches and other kinds of cyberattacks.
- Improves security posture – As organizations can proactively identify and mitigate threats before they even occur, it can help them maintain a strong and resilient security posture.
- Better threat visibility – With continuous monitoring, cybersecurity teams can also get a clear visibility of their attack surface and know if there are any security gaps easily.
- Faster response to threat – Not only proactively identify threats but CTEM can also assist with faster remediation of vulnerabilities, which can minimize the attack window for cybercriminals.
- Compliance with standards and regulations – Implementing CTEM, organizations can also ensure compliance with regulatory requirements and industry standards as they can provide proof of continuous security monitoring and prevention steps.
Seeing these benefits, we can imagine how useful CTEM is for organizations in strengthening their overall security posture and saving huge costs dealing with cyber-attacks and their aftereffects.
Conclusion
Continuous Threat Exposure Management (CTEM) is undoubtedly an advanced technique to ensure overall security by continuously monitoring for threats and vulnerabilities. As it uses advanced technologies, including AI and machine learning, it gets an edge over traditional vulnerability management processes and helps mitigate threats much before they even occur.
As we move further in 2025 and the years to come, we will see CTEM becoming an essential component of an organization’s security. It will help organizations automate their security tasks and enable them with a proactive approach towards cyber-attacks rather than a responsive one.
Therefore, organizations need to actively adopt this to understand and neutralize threats to avert heavy future damages.




