

How to Command Online Privacy in 2025 - Meaning and Tips Explained
Why is defending your cyber presence essential in today’s times? Just for the simple reason of safeguarding your data and critical information from being misused. Malicious threat actors are everywhere, on a lookout to compromise your hard-earned reputation and impact you financially and emotionally. This leads to researching ways to protect yourself with sheer online privacy that cannot be infiltrated by any such threat actors.
Google Cloud’s Cybersecurity Forecast 2025 Report reveals trends that will shape the future of cybersecurity. From the increasing use of AI by malicious actors to the impact of new regulations, this report offers a comprehensive look at the threats and opportunities on the horizon. A deeper focus on securing cloud environments with Cloud Security Posture Management (CSPM) tools and robust identity controls are some of the essentials that need to be catered to at the outset.
Adding to the threat concern, Cybersecurity Ventures expects the global cybercrime costs to grow to US$ 10.5 trillion annually by 2025. This is a striking number, impacting the global GDPs and strategic businesses adversely. Deepfakes and AI-generated content are the most widely used tactics to crack into your cybersecurity. This is why it is essential to build robust security walls with the right plan in place, and it all starts by clearly understanding what online privacy truly means and comprehending the nuances revolving around it. Let us dive straight in!
Understanding Cybersecurity Concerns
- The social media Facebook has been a particular focus of privacy concerns on the internet. Users tended to fall back on Facebook’s default settings, which, due to Facebook’s ‘opt-out’ policy, were at the loosest level of security, forcing users to opt-in to make information private. Over the years, this policy norm was revised by the company.
- Google’s street view photo-mapping service caused privacy concerns when the company disclosed that it had been recording locations and some data from unprotected household wireless networks as it took pictures. The data was gathered inadvertently. German officials objected to Google’s actions, based on Germany’s strict privacy laws, and although German courts decided against the objections, Google did not expand its Street View service in Germany beyond the handful of urban centers that it had already photo-mapped.
These instances are some of the popular real-world examples that led to a deeper understanding of online privacy and the criticality of mastering ways to handle it securely.
Online Privacy
Online privacy, aka Digital privacy, is essentially the same thing, referring to the ability to protect and control your personal information while using the internet and online platforms. This encompasses the protection of personal information, communications, and activities while online, including browsing, financial data, and other potentially vulnerable data. It is about having control over how your digital information is collected, stored, processed, and shared online. This includes protecting your personal information from unauthorized access and misuse, such as identity theft or fraud. Caring for your online privacy helps keep your information private and secure, thereby protecting you from various kinds of theft, including ransomware and diverse phishing attacks.
What is at stake?
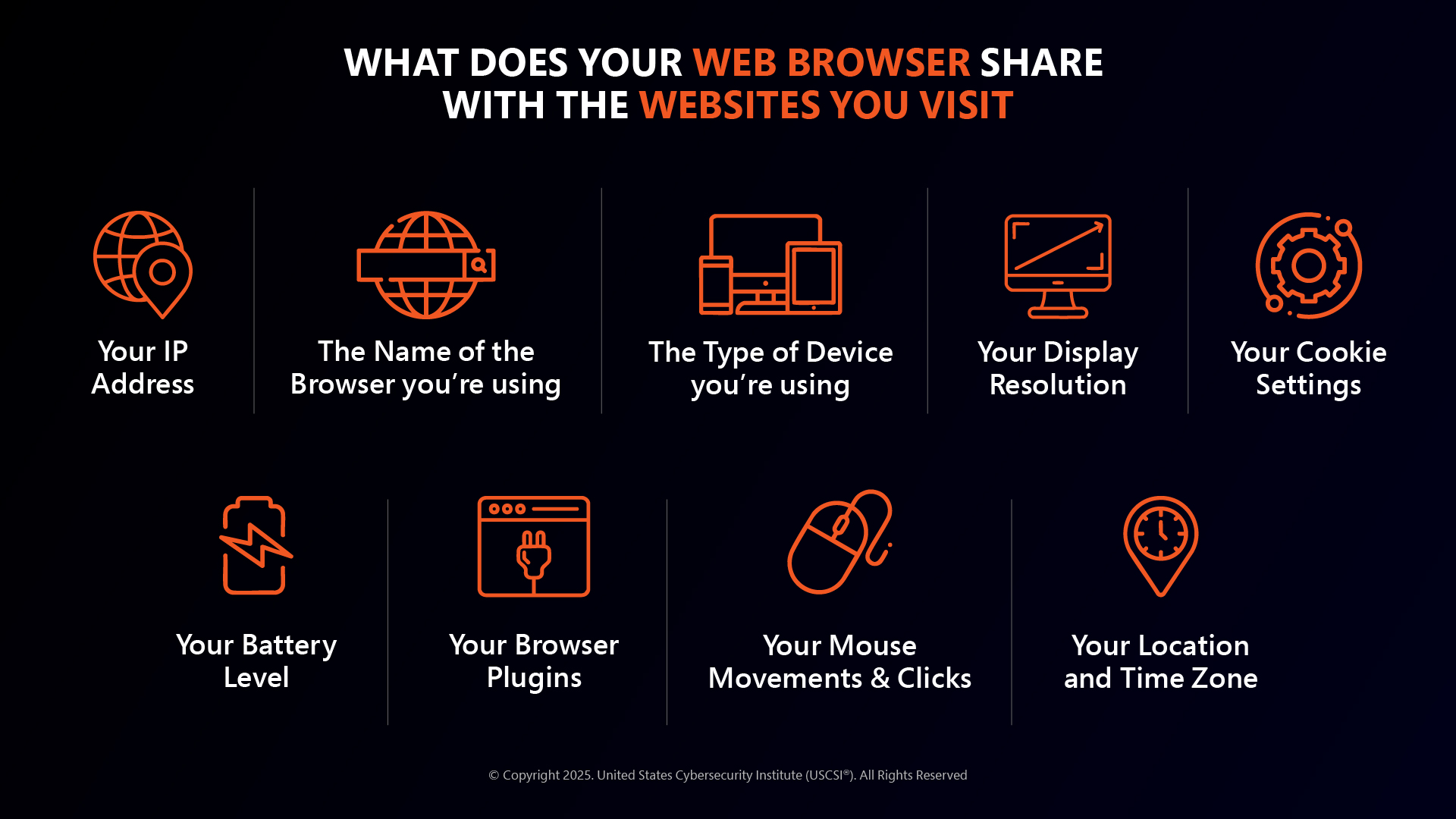
Looking at the above imagery, this makes it quite clear what is at stake and what needs to be guarded at all cost. From your IP addresses to browser plugins, your mouse click movements, you are under surveillance on the web 24/7.
Privacy vs Security
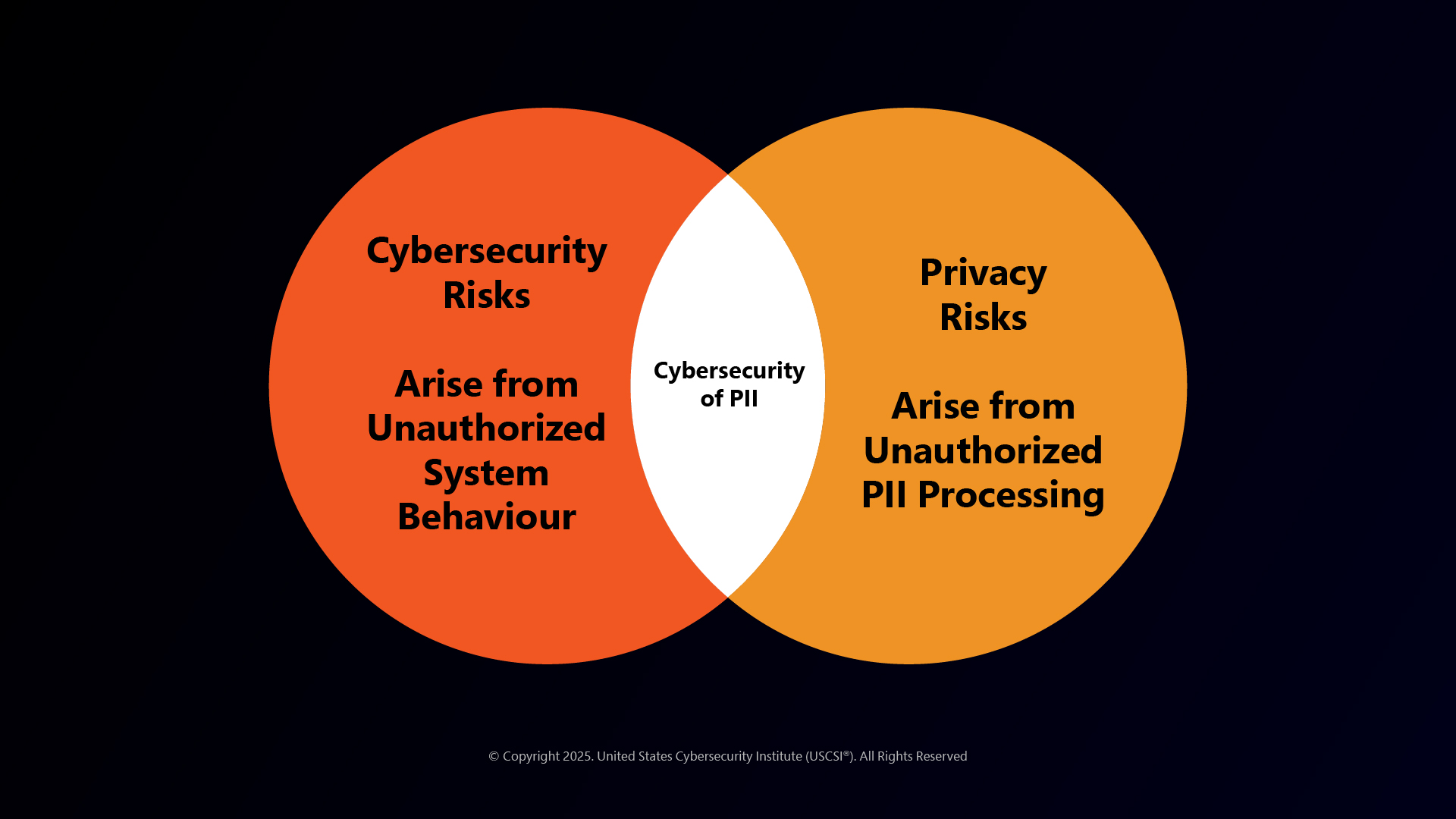
However, understood under a similar framework, online privacy and cybersecurity differ minutely in action. While both online privacy and cybersecurity are crucial aspects of protecting digital information, they differ in focus. Cybersecurity focuses on protecting systems and networks from unauthorized access and attacks, while online privacy focuses on protecting personal information and how it is collected, used, and shared.
Cybersecurity looks like implementing firewalls, antivirus software, intrusion detection systems, and secure coding practices. Whereas online privacy includes using strong passwords, enabling two-factor authentication, and limiting data sharing on social media. Whereas the goal of cybersecurity is to ensure confidentiality, online privacy may aim at maintaining control over personal data and ensuring its confidentiality and ethical handling throughout.
What makes Online Privacy essential?
A clear message comes across as to why online privacy matters in real space. By securing your online presence, you as a user can easily protect against burgeoning cyberattacks that widely comprise your sensitive information, deemed not to be shared in the public domain. Protecting your online privacy acts as a barrier against these malicious actors by reducing the amount of exploitable data available on the internet, making it more challenging for them to carry out their attacks successfully.
With greater security comes greater control over your data online. As the creation of target ads and product recommendations are all streaming from your online present data, it needs to be guarded well to be used efficiently and not by malicious threat actors.
Legislative Rules Governing Online Privacy
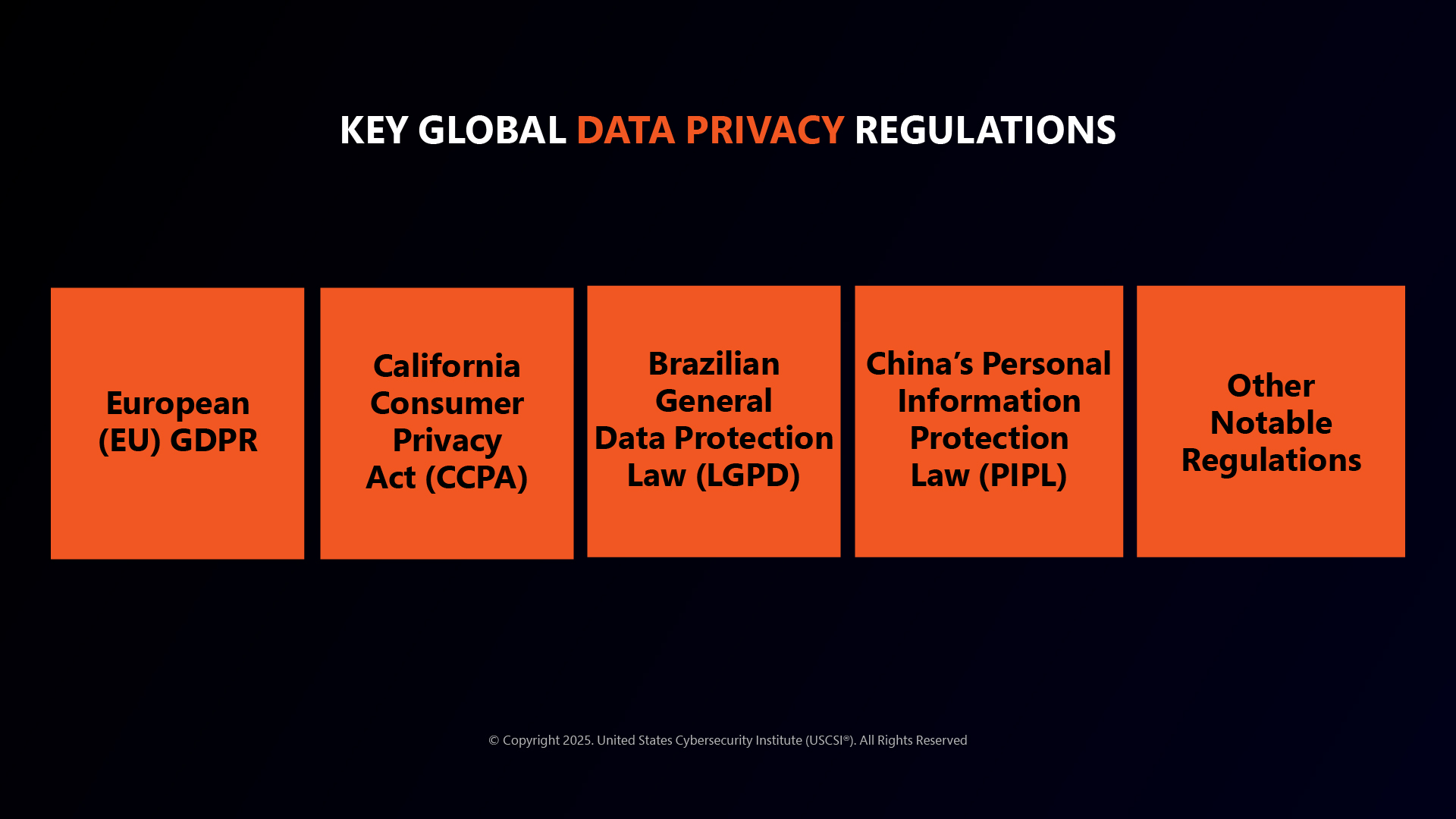
- EU GDPR- Concerns right conferred to individuals and the extraterritorial scope impacting businesses beyond the EU.
- CCPA- Emphasizes consumer rights, opt-out mechanisms, and obligations imposed on companies to disclose their data practices.
- LGPD- Includes understanding the rights of Brazilian data subjects and the compliance obligations for businesses operating in Brazil.
- PIPL- Addresses the protection of personal information, exploring its implications for data processing, cross-border data transfers, and the rights of individuals.
- Other Significant regulations include the Personal Data Protection Bill (PDPB) in India and the Data Protection Act in the United Kingdom post-Brexit.
How to Build Robust Online Privacy?

Look into the encryption strength and encryption key length while using a VPN network. Configuring your browser, changing your search engine often, using an anti-virus and firewall software, changing social media privacy settings, securing your emails, creating secure passwords, and using secure payment methods are some of the key steps to remember while staying secure online. Do not think twice to indulge in understanding the core of cybersecurity with the best cybersecurity certifications; to gather a detailed understanding of ramping up your online security and revitalizing your presence over again; as the threat landscape become vicious with every passing year. Stay alert!




