

Cybersecurity Transformation: Everything You Need to Know
With the threats evolving rapidly and becoming highly advanced, innovative, and more sophisticated, organizations are employing numerous techniques to shield themselves from such attacks. Cybersecurity transformation is one such important strategy aimed at improving the overall security posture of any organization.
It is a strategic and comprehensive shift in how modern-day organizations attend to the security challenges they are facing today and implement the best security practices. It is not just about updating the cybersecurity tools and technologies but a fundamental shift in organization’s mindset, processes, and culture.
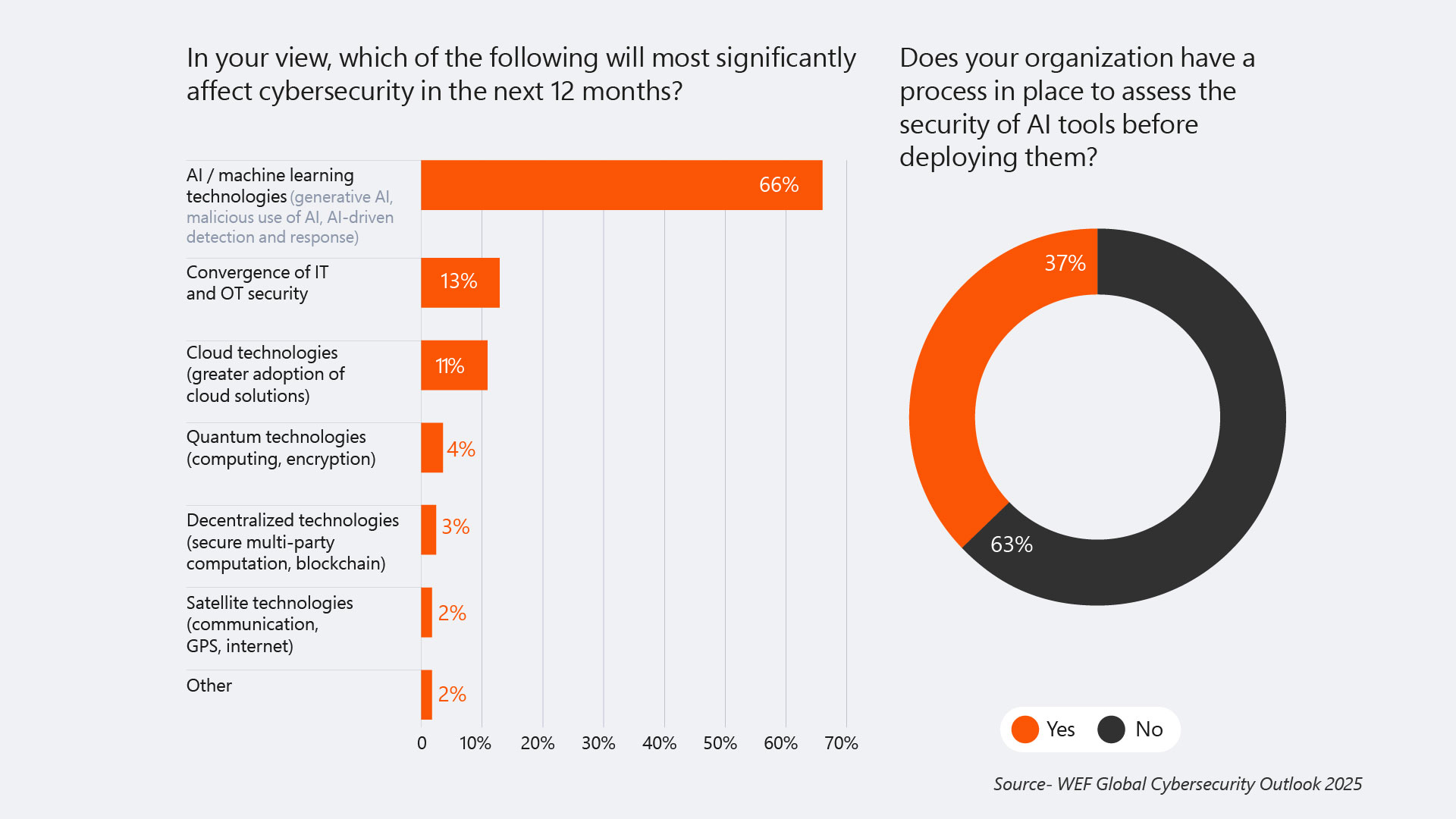
Now, digital transformation is on the rise and the same technology can pose greater threats. 66% of organizations believe AI and machine learning will have a huge impact on their organization's security in the next 12 months (WEF Global Cybersecurity Outlook 2025).
Key Aspects of Cybersecurity Transformation
The process of cybersecurity transformation is quite complex and requires the careful attention of cybersecurity specialists to implement it properly and safeguard the organization’s critical infrastructure and data.
Here are some of the key aspects that determine effective cybersecurity transformation:
- Holistic strategy
Cybersecurity transformation aims to create a unified cybersecurity strategy that includes all the essential cybersecurity domains such as risk management, threat intelligence, incident response, compliance, etc.
- Align with business goals
It shouldn’t be perceived as a different IT function but must be integrated into the overall business strategy and aligned with the organization’s business goals to assist with its digital transformation and innovation.
- Adapt to emerging threats
The threat landscape is evolving at a much faster rate than we can imagine. Cybersecurity transformation helps build a flexible and adaptable security measure to meet evolving as well as emerging cybersecurity challenges promptly.
- Focus on proactive measures
Cybersecurity transformation takes organizations from a reactive to a proactive approach so that they can detect and eliminate threats early.
- Governance and compliance
Another important aspect of cybersecurity transformation is that it takes care of governance and compliance with security standards and regulations too.
This strategy empowers cybersecurity professionals and other employees in the organization to become security conscious and understand their role in protecting sensitive data. Additionally, it may also consider upgrading existing cybersecurity solutions and infrastructure, offering cybersecurity certifications to employees, providing essential cybersecurity training awareness and education, etc.
The Importance of Cybersecurity Transformation
The importance of cybersecurity transformation cannot be understated in today’s highly interconnected and digital world where cyber threats are constantly looming over organization’s systems and data.
Today, organizations are actively adopting cloud infrastructure and remote work culture. The use of IoT devices is on the rise. These factors have made traditional IoT security and other security techniques obsolete considering the huge attack surface they create.
Moreover, cybercriminals are now using advanced technologies like artificial intelligence and machine learning to carry out attacks in more innovative ways on a large scale to exploit vulnerabilities which has led to an increase in the number and cost of cybercrimes.
So, cybersecurity transformation provides organizations with a foolproof cybersecurity solution involving the integration of advanced tools like AI-driven threat intelligence, effective IAM, zero trust frameworks, and more to keep them protected.
Benefits of Cybersecurity Transformation
Now, let us explore how organizations can benefit by integrating cybersecurity transformation.
- Reduce the risk of cyberattacks
The biggest benefit is of course reduction in cyber-attacks. This cybersecurity approach offers better risk management to protect against all kinds of cyber threats.
- Simpler security architecture
A lot of cybersecurity tools and solutions are often used that make cybersecurity operations complex requiring cybersecurity specialists and numerous resources. Cybersecurity transformation can unify these scattered solutions and make the overall security architecture simpler.
- From legacy to cloud infrastructure
Still, for many organizations, the traditional on-premises and legacy infrastructure is the preferred choice. Integration of cybersecurity transformation can mark the start of their journey from legacy to cloud infrastructure offering more flexibility and scalability.
- Minimize implementation and procurement time
Organizations face a bigger challenge of successfully implementing advanced cybersecurity tools taking up a lot of cybersecurity expertise and time. Cybersecurity transformation minimizes this and can speed up implementation and procurement time.
Steps to Implement Cybersecurity Transformation
Now that you understand the importance and benefits of cybersecurity transformation, you must know how to implement it successfully in your organizations. So, here are the key steps cybersecurity leaders must follow:
- Top management must lend their support and commitment to implement a robust cybersecurity strategy aligning with their digital transformation goals
- They must evaluate their existing security systems and vulnerabilities across cloud, IoT, networks, etc.
- Next, the key stakeholders including cybersecurity leaders, employees, IT, and cybersecurity professionals must engage and collaborate to offer greater insights and better solutions.
- Then define your security goals such as budget, timelines, compliance, etc.
- Afterwards, a clear roadmap must be designed on how to achieve the goal in a SMART way.
This way, organizations can successfully implement cybersecurity transformation. After that, the security teams must also conduct continuous audits and assessments, track the KPIs related to risk management, and improve continuously for the best security posture.
Challenges To Successful Cybersecurity Transformation Implementation
Integrating cybersecurity transformation with digital transformation can surely make the organization more secure and protected against all kinds of cyber threats. However, cybersecurity leaders need to certain barriers for its successful implementation such as:
- Resistance to Change: New tech and cultural shifts meet internal opposition.
- Talent Shortage: Lack of skilled staff hinders implementation. The cybersecurity skill gap has grown by over 8% since 2024 and only 14% of organizations are confident about their security workforce.
- Technology Complexity: Integrating new tools with existing systems is challenging.
- Budget Constraints: Investments in tech and training require clear ROI to justify costs.
Future of Cybersecurity Transformation
The future of cybersecurity transformation will emphasize more on agility and integration. As the technology evolves and cybercrimes become hard to identify and mitigate, organizations will be leveraging transformed infrastructure to combat with such new and emerging cyber threats such as multi-cloud, IoT, and AI. This will include proactive security and a focus on zero trust and secure-by-design architecture. These techniques will be included into the core of the security systems. Advanced IAM, AI-powered threat and detection and response, and machine learning for anomaly detection will be on the rise.
So, it becomes the responsibility of cybersecurity leaders to seamlessly integrate innovative security technologies to ensure their organization is cyber resilient and induce confidence in business decisions without worrying about risks and compliance.
Conclusion
This is an era of digital transformation and while making their organizations digital, the business leaders should neglect the importance of keeping their infrastructure and data secure. This is where cybersecurity transformation comes into play, aligning with business goals and keeping critical assets protected from evolving and emerging cyber threats. With proper consideration, planning, and effectively addressing the associated challenges, leaders can successfully implement cybersecurity transformation can keep their organizations shielded.




