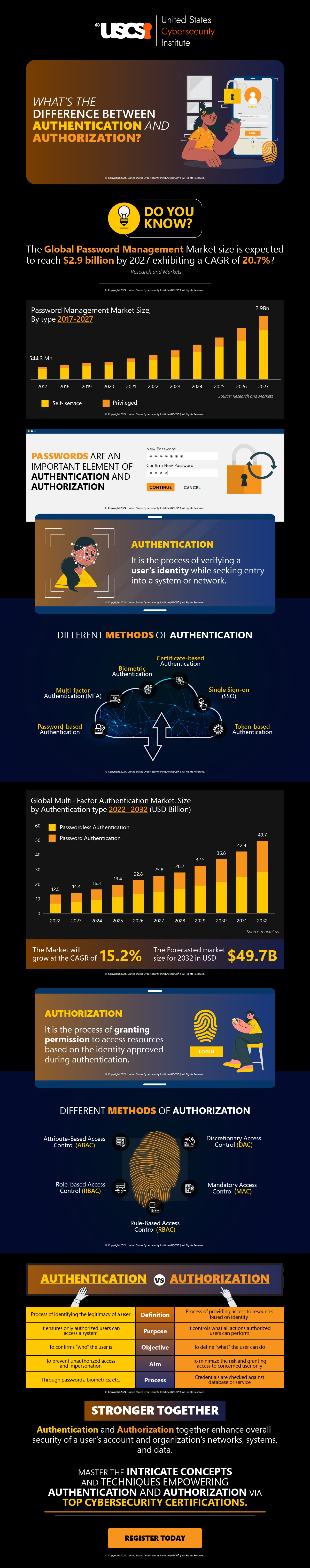
What’s the difference between Authentication and Authorization? | Infographic
The terms authentication and authorization, though sound similar, are significantly different. For example, imagine entering a high-security building. The first checkpoint will be authentication where your identity will be verified at the entrance where you need to show genuine ID. And the authorization process is like having a proper keycard to access specific areas in the building.
The same is the case in the digital world where authentication and authorization combinedly offer a high level of security to your data and devices. The authentication process is used to verify a user’s identity. They are typically in the form of login credentials like usernames and passwords. And after the users are successfully authenticated, the authorization process determines what actions they can perform and what data they can access.
You will be surprised to know that the global password management market is expected to reach a staggering $2.9 billion by 2027 growing at a CAGR of 20.9%.
Passwords, multifactor authentication (MFA), biometrics, etc., are some of the authentication factors. On the other hand, authorization is often based on user roles and levels of permission. For example, if you are working in the sales department, then you may not have authorization to access data in the finance department.
In the following infographic, we discuss various ways of authentication, and authorization, and briefly compare their differences and use cases.
Explore the infographic guide and understand how authentication and authorization are essential for securing data and devices.