

What are the Information Security Principles to Enhance Business Security?
The world is growing toward cyber-controlled warfare. Processes and business systems worldwide are guided by virtually secured systems. With data creation expected to reach 147 zettabytes by the end of 1014 (edgedelta.com); the need to secure your cyberspace is a must. Isn’t that a massive reveal that cybersecurity has become the guiding force controlling a major chunk of this sensitive data generation? It is time to leverage cybersecurity skills to gain control of your data online.
This whopping data surge is commanded by the growing popularity of social media, which has led to people relying on the internet to meet their daily needs. Also, when you talk of cybersecurity, it should not be taken as the same as Information security. Let us dig deep and understand the difference and how is information security pivoting the wagon ahead with its core principles.
What is Information Security?
Information security (Infosec) is a set of information technology practices, methodologies, and tools that give access to information security professionals to protect the organization’s data assets from malicious cyber and information security threats. It aims at guarding a variety of enterprise data, including Intellectual property, business secrets, consumer data, financial data, and other types of private information. Statista reveals that global security services dominate the market with a projected market volume of USD 92.91 billion in 2024. This is a clear win situation for deploying and understand the core of Infosec in-depth NOW!
Objectives of Information Security:
Understanding the motive or the drive behind safeguarding your content via information security analysts is a critical task. Objectives are:
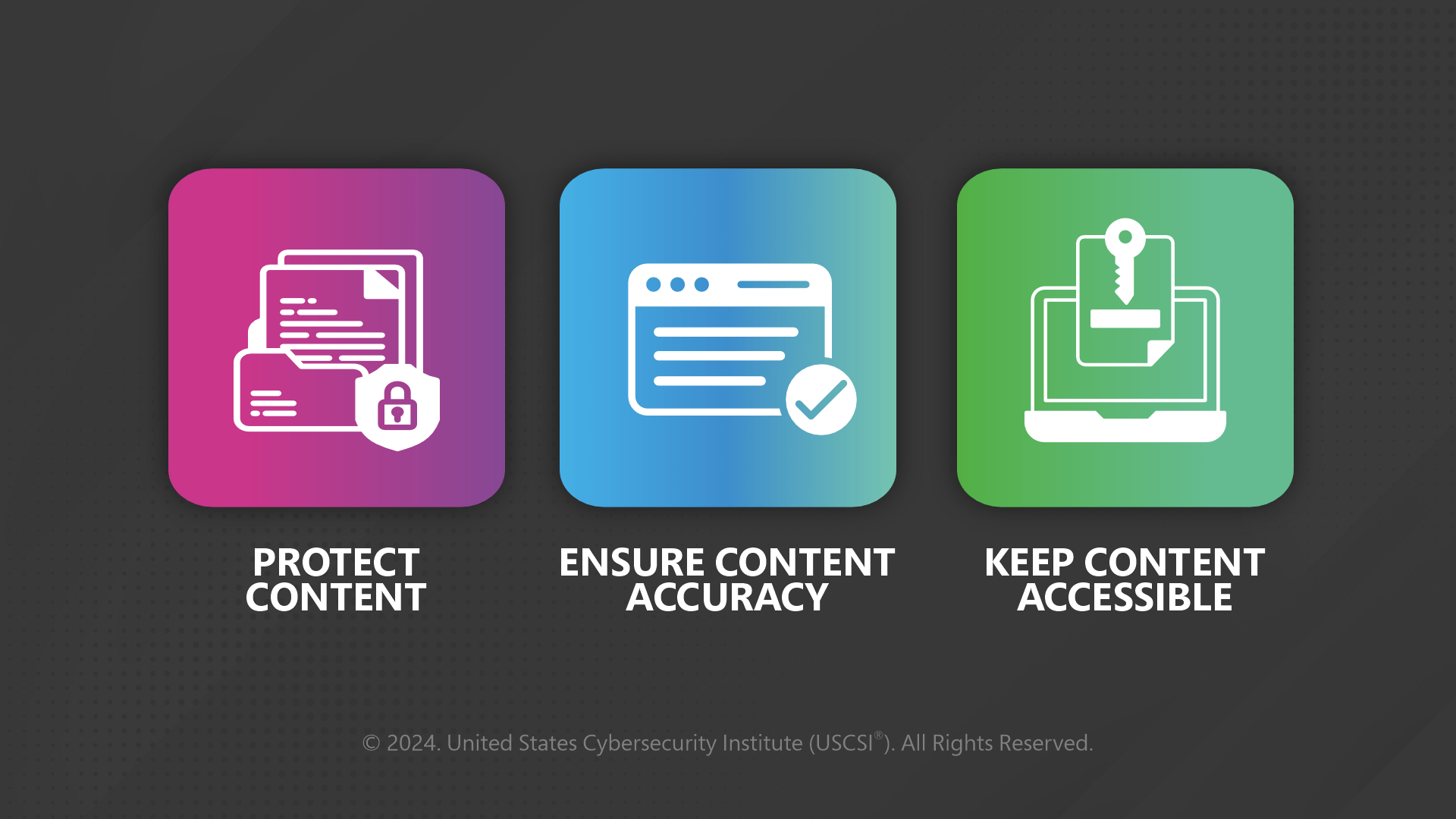
These objectives require a knack of balance that will determine the destiny of the entire information security wagon.
- The foremost way to balance is to keep your eyes on the risks at hand
- Confidentiality and integrity go hand in hand. Limit the access to your content by using a cloud backup program
- Automated malware detection can assist big time in controlling the menace
Information Security vs Cybersecurity:
Same but different! These two terms look identical but cater to diverse arenas of cybersecurity. Cybersecurity is the strategy used to protect against cyberattacks; whereas Information security is a broader term incorporating cybersecurity. It can be easily said that cybersecurity is a critical subset of information security. Infosec stands for protecting all kinds of information and assets.
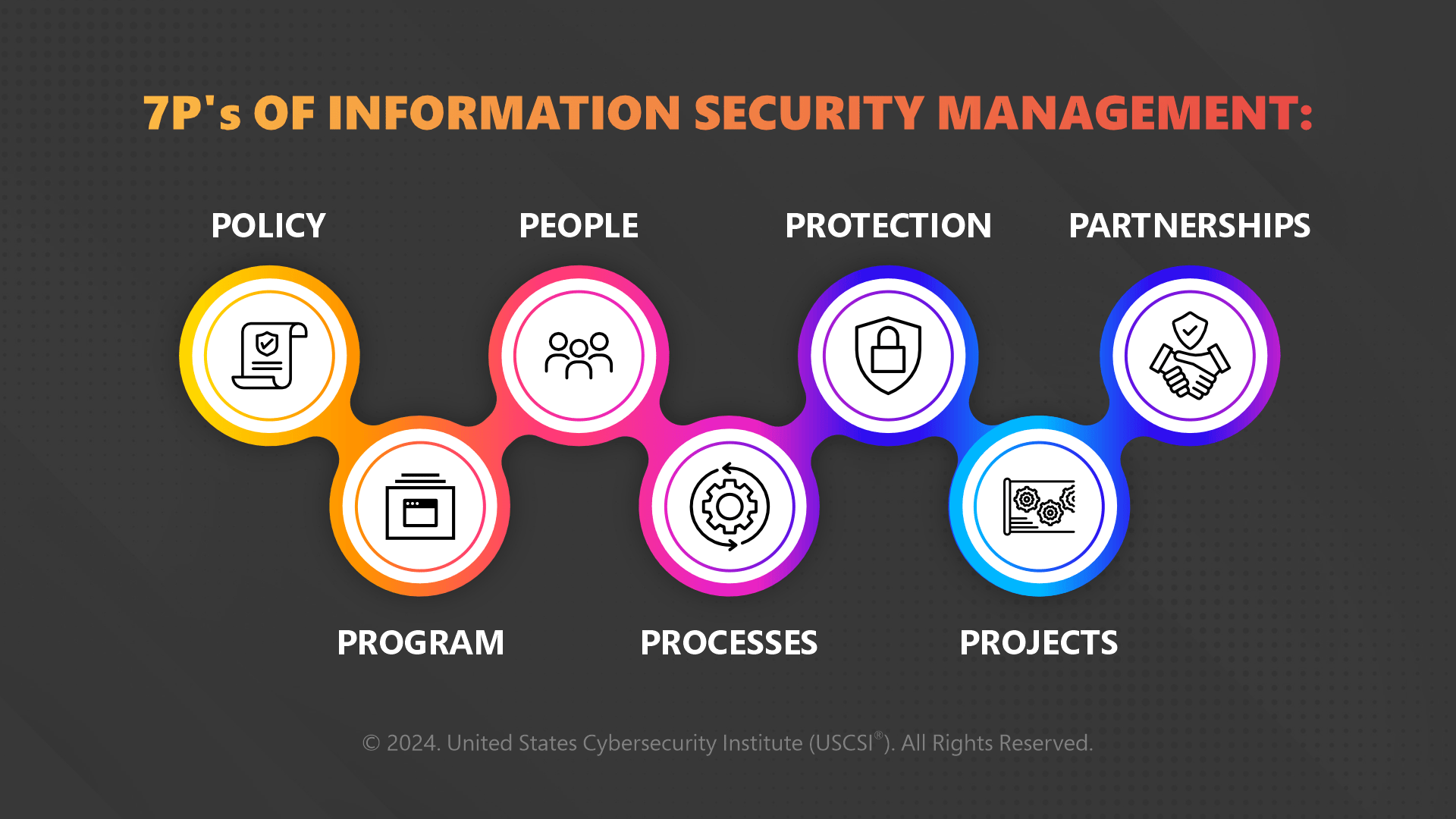
These 7 Ps form a strong baseline for securing your information online. These can efficiently guard your information from malicious threat actors online. From
- Defining and establishing information security policies and norms to
- Strategic planning;
- Creating awareness among employees about security risks;
- Streamlining workflows and procedures;
- Deploying technical and physical measures;
- Managing infosec initiatives and system upgrades; and
- Emphasizing the role of collaboration among teams and stakeholders.
You are safe if you follow the core strategies to secure information online.
7 Information Security Threats:
- Viruses that can auto-replicate and spread automatically
- Malware that bypasses enterprise security systems to infect enterprise networks
- Ransomware that encrypts data or locks users out of their systems
- Phishing scams trick victims into revealing confidential information
- Drive-by download attacks download a malicious code from a website to a system
- Insider threats steal credentials and valuable enterprise data
- Advanced Persistent threats penetrate the enterprise network and remain undetected
3 Principles of Information Security:
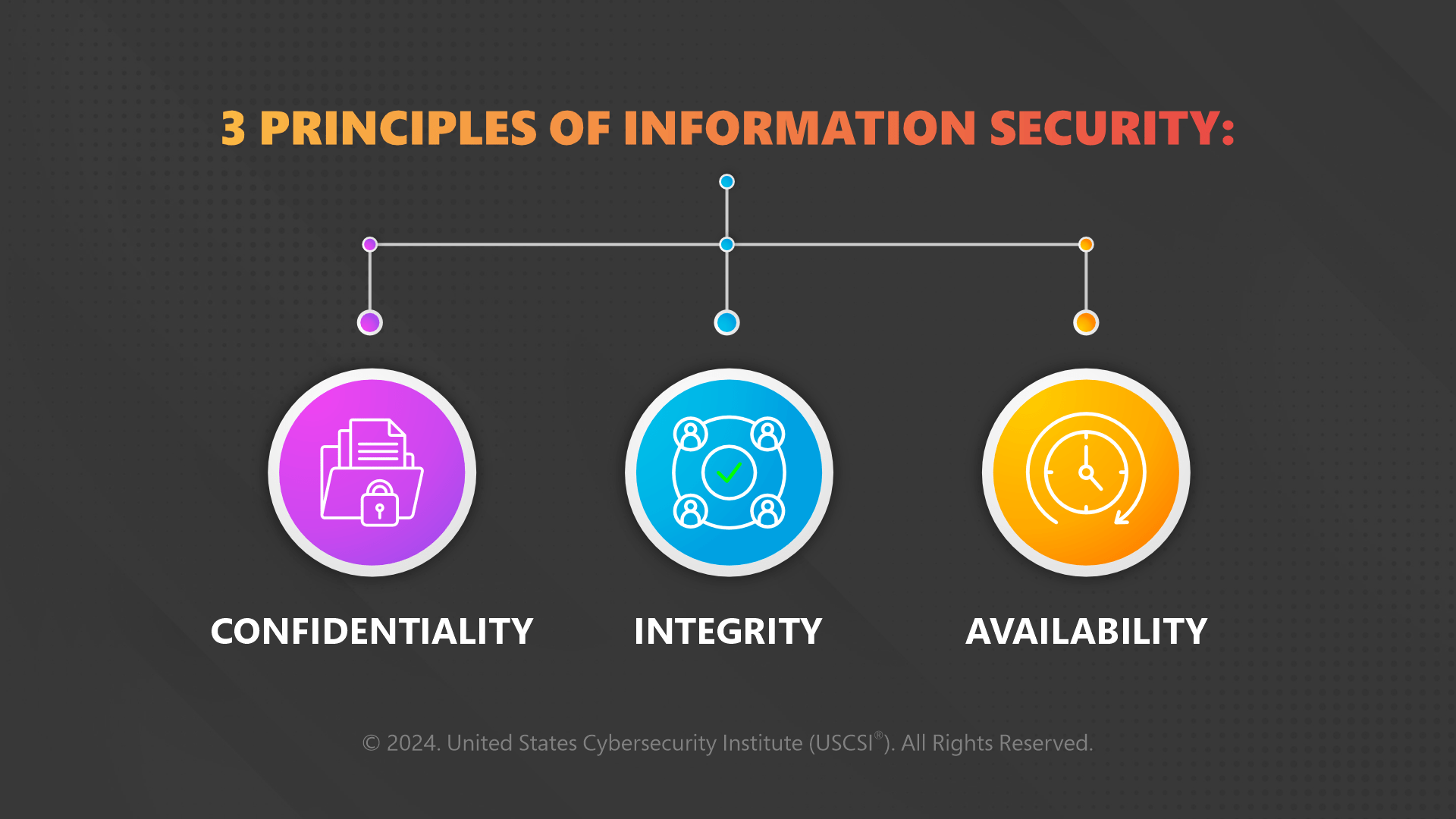
- Confidentiality
It commands massive respect as it is highly crucial to secure information and makes it available to authorized personnel only. Unauthorized people must be barred from data access, which is accomplished by verifying the authorization of individuals trying to gain access to the information. The popular controls to be deployed include identification, authentication, authorization, and encryption.
- Integrity
This one is next to take on the spotlight as no confidentiality procedure is complete without integrity. Protection of data integrity or information integrity requires additional procedures. Backup controls enable you to restore access to destroyed information, audit logs let you understand who has changed a specific piece of information.
- Availability
Set up access control for the right people and train them on security measures so they can assist you in keeping the information secure. Attend to the following factors while designing an availability procedure:
Where>> How>> When to access the information?
3 Information Security Controls:
- Authentication
It involves identification controls, passwords, and two-factor authentication that protect the confidentiality of your content online. They impact content availability, as employees with the requisite permit can use the right passwords to secure data.
- Access Control
It involves content classification, time-bound links, and updated access lists. These help in ensuring the new employees get the permissions they require to begin performing their tasks promptly and efficiently; without a hassle.
- Encryption
Content encryption allows you to control its confidentiality and integrity. The length of the key determines its strength and effectiveness. Encryption protects the content when it is not active on the web and is being transmitted from one system to another easily.
Final Word:
Protecting the information on the web for a company and businesses worldwide is a much larger concern than in any other area. It is advised to build a strong shield of security against malicious online threats by designating specialized information security analysts, duly certified in the best cybersecurity certification programs. Your business is sure to scale with the best nuances and strategies deployed by top-of-the-line professionals with the most futuristic cybersecurity skills on display. Hire the best to differentiate and enable stronger and safer business roots worldwide!





