

Understanding the difference between Black, White, and Gray-Hat Hackers
The term hacker is often perceived as a shadowy figure focused on high-end computer systems and looting banks and individual systems. At least this is what is shown in movies and shows. But the reality is entirely different. This is not as glamorous as it is shown in movies but a very complex and sophisticated process.
Hackers come in various shades, they can be good, bad, or even both. What differentiates is their motive for hacking. Whether they are hacking a system to exploit it or want to make it stronger, depending upon their purpose, they can be categorized as white hat hackers, Gray hat hackers, or black hat hackers.
In this article let us explore the key distinction between these three popular types of hackers and what their intentions are, what methods they use, and how they impact the world of cybersecurity.
Black Hat Hackers: The Dark Side of Hacking
As the name suggests, they can be easily identified as criminal hackers whose only motive is to create havoc in the digital space. They represent the most unpopular side of the hacking world and their purpose of hacking is personal gains which can be achieved by disrupting organizations' normal working, financial theft, data breaches, disrupting important infrastructure, or maybe even launching cyberwarfare.
They have mastered cybersecurity skills and their hacking method is usually destructive as they do it by deploying malware (malicious software), exploiting vulnerabilities, and employing social engineering strategies to gain access to and infiltrate systems.
As per a study by IBM Security X-Force Threat Intelligence Index 2023, there is a significant growth in the ransomware attacks carried out by black-hat hackers and the average ransom demand has increased by over 13%. This huge number indicates their impact is only growing and that they are exploiting vulnerabilities at large scale.
Another report by Cybersecurity Ventures predicted that global cybercrime costs will reach $10.5 trillion annually by 2025. So, the black-hat hackers continue to be a constant threat to both individuals and organizations (private and government). Organizations therefore seek cybersecurity professionals to combat such increasing attacks.
White Hat Hackers: Protectors of Cyberspace
They are good hackers whom we popularly known as ethical hackers. Ethical hacking is among the most popular cybersecurity career paths as well and students and professionals engage themselves in a variety of cybersecurity certification programs to learn this cybersecurity skill.
These cybersecurity professionals use their hacking skills to identify and patch vulnerabilities within their organization's computer and network systems. They often work independently and are hired by security firms and government agencies, and maybe even by organizations for full-time work to strengthen their overall security efforts.
Ethical hacking is also known as penetration testing in which the white hat hackers simulate cyberattacks in a controlled environment with proper authorization to expose weaknesses, generate reports, and suggest suitable mitigation strategies. This helps organizations to strengthen their systems and networks before they are exploited by real hackers.
Gray Hat Hackers
Their role isn’t clearly defined in the world of cybersecurity. Though their intentions to hack a system or network may not be malicious, their methods are questionable. That means they might hack a system without proper consent or authorization. The motive can be to test their cybersecurity skills and expertise, betting, or notify the owner about the system vulnerabilities but openly in a public forum, or for any other purpose.
In some cases, Gray hat hackers have also offered to fix the vulnerabilities by themselves after identifying vulnerabilities through hacking without proper permission. This act of kindness is actually blurry and doesn’t clearly distinguish between ethical and exploitative behavior. Therefore, their actions can have serious consequences which makes it difficult to label them as good or bad, thus, they are Gray-hat hackers.
If you are looking to get into a cybersecurity career, it is highly recommended to earn a cybersecurity certification and learn the latest skills to protect an organization’s digital infrastructure and sensitive data from hackers.
Distinguishing Factors Between Black, White, and Gray-Hat Hackers
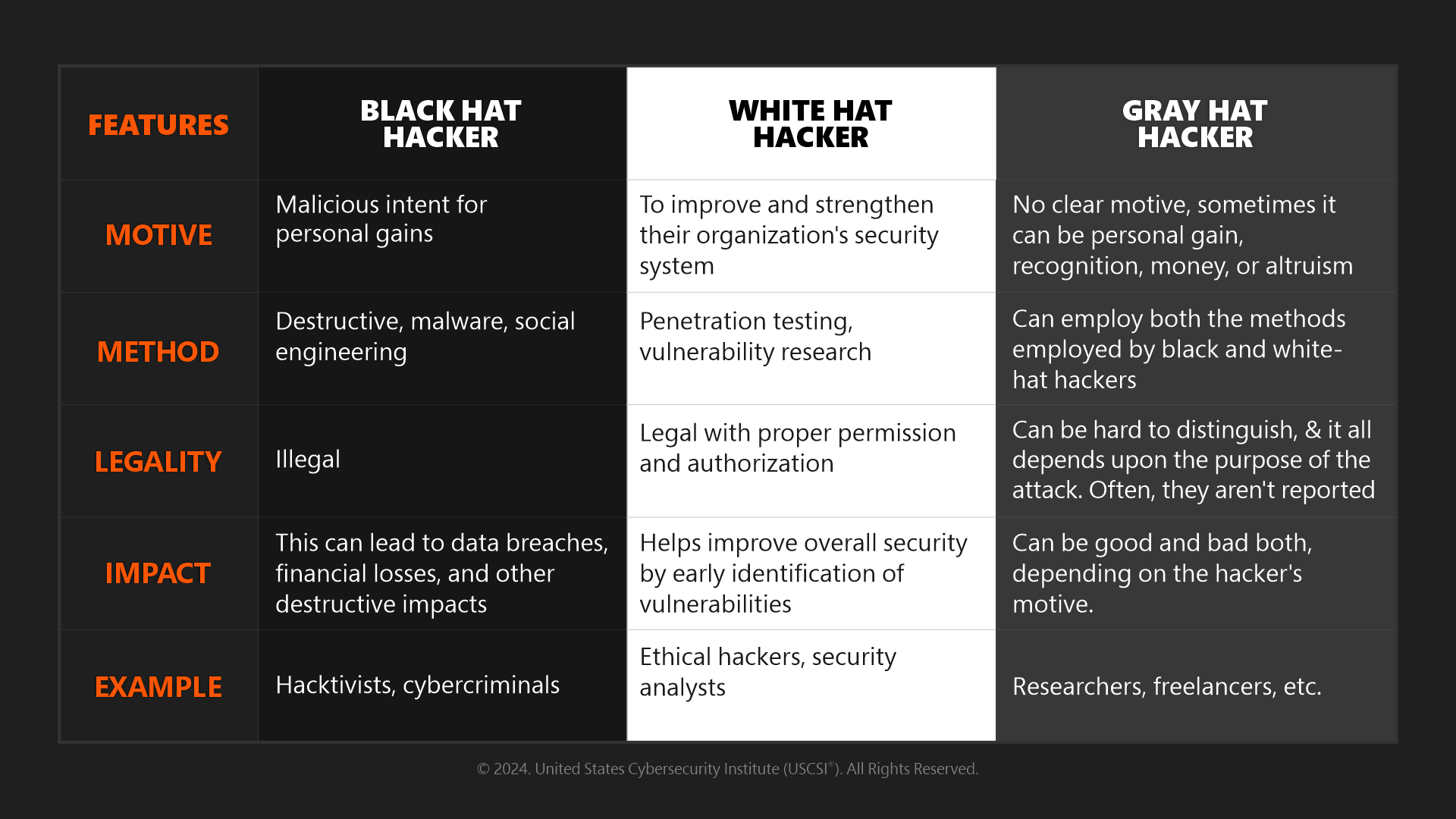
Conclusion
The world of hacking isn’t clear and straight. The black, white, and gray-hat hackers represent different motives, and methods, and can have different impacts. Therefore, it becomes essential to recognize the difference between these three forms of hacking if you are dedicated to making a career in this field. The world of cybersecurity is evolving rapidly with advancements in technology, and organizations have started giving due respect to ethical hackers by offering them full-time designations like penetration testers or ethical hackers.





