

Phishing Or Spear Phishing: Which is More Vicious?
Cybersecurity is a game attackers play with higher precision than cybersecurity professionals. Don’t you think so? This is why the rate of cybercrime is growing at an astounding momentum in every passing year. The Cybercrime Magazine states a report by Cybersecurity Ventures that in the year 2024, the global cybercrime damage costs shall reach a whopping USD 9.5 trillion annually. This showcases the magnitude of cybercrime taking place every passing second.
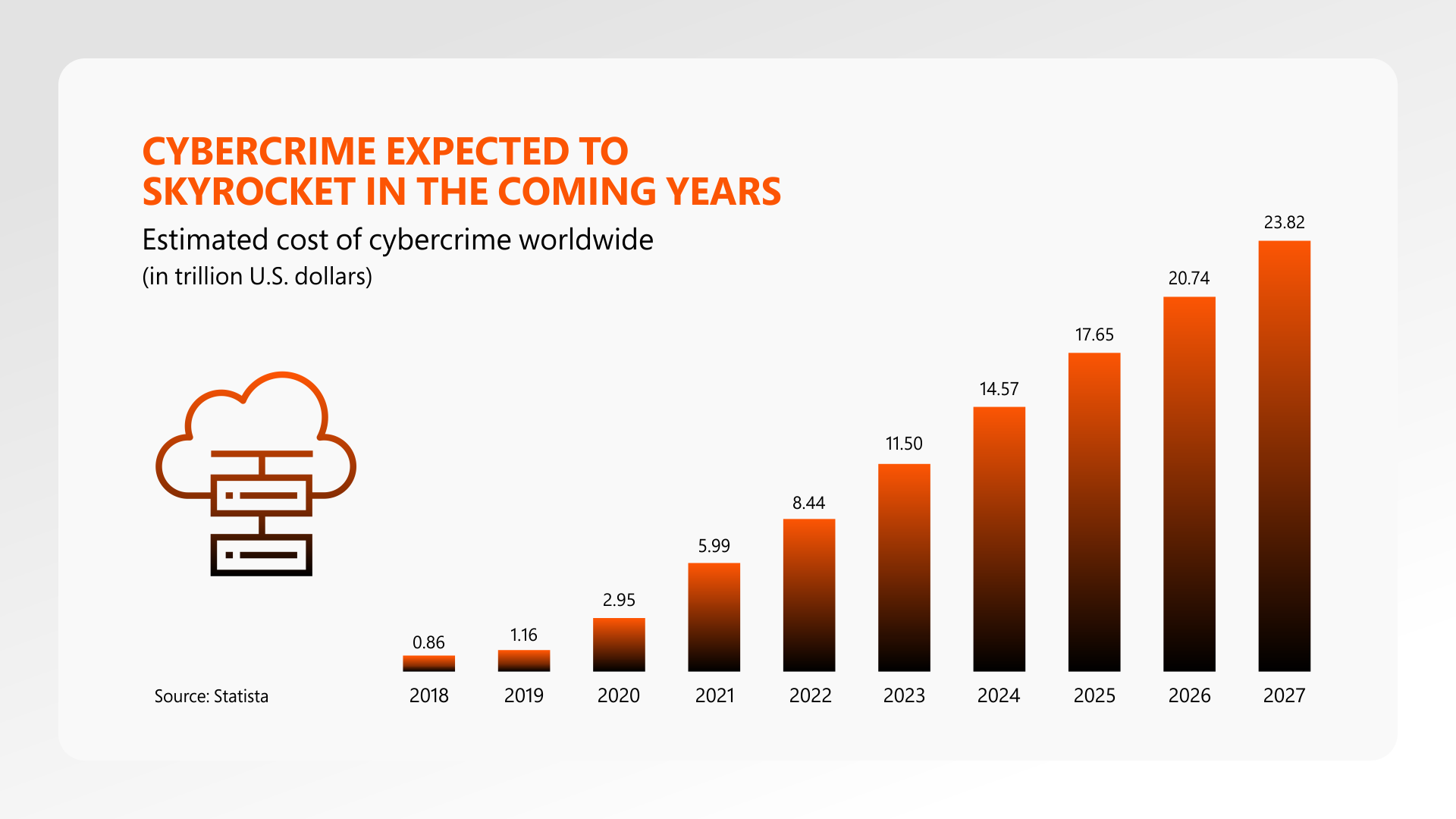
The numbers revealed above by Statista highlight the enormous growth of cybercrime rates over the years. This is the time to put your guard on and earn the best cybersecurity certifications from credible credentialing bodies.
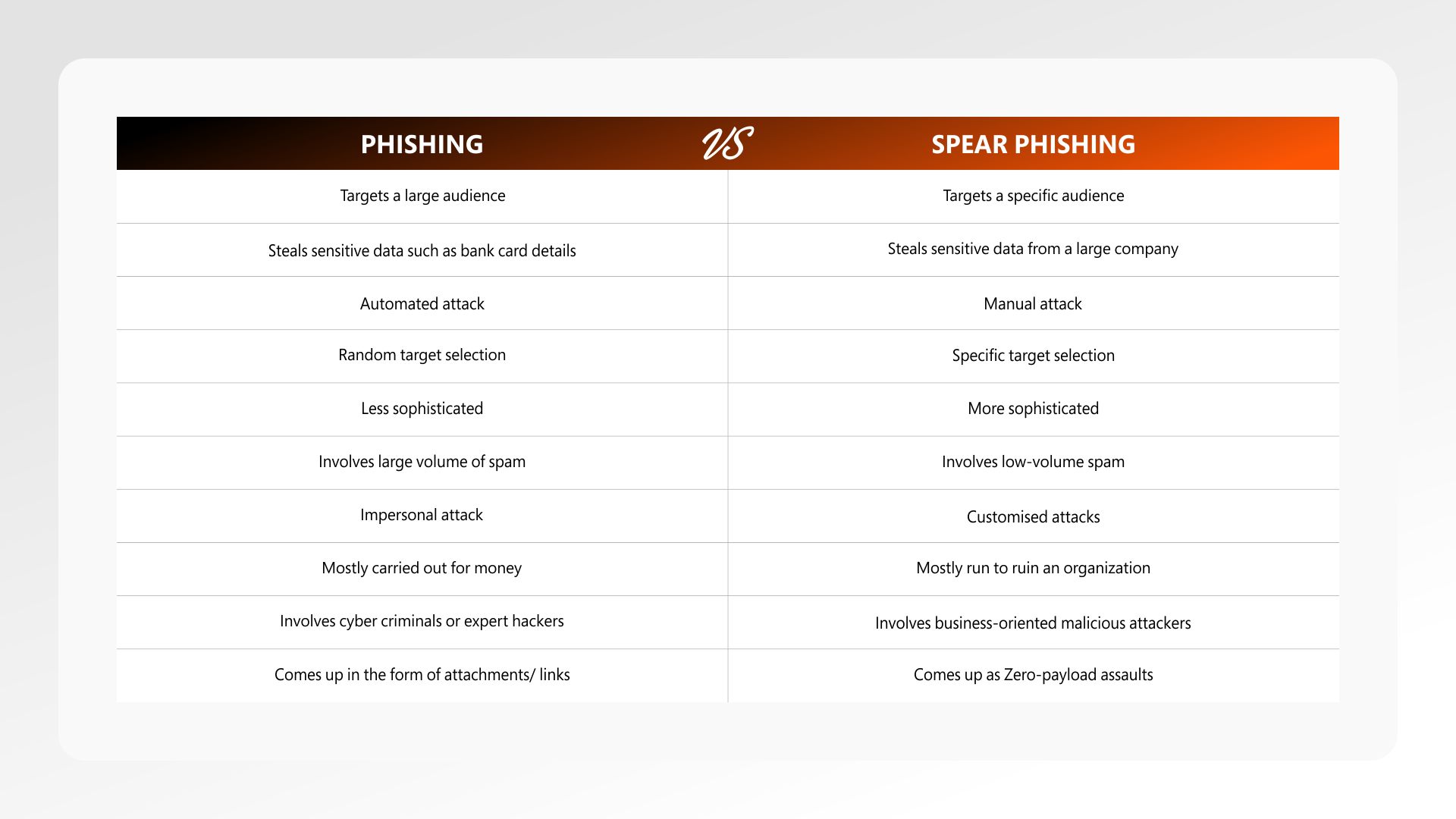
Here is the time to understand the most vicious on the block that are making waves in the realm of cybersecurity crimes.
Phishing
Phishing attacks are spreading beyond emails to text messages and other forms of personal communication. The most common impact of phishing attacks on small and medium enterprises is sensitive data loss. CNBC highlights a 173% spike in phishing volumes in Q3 last year as against the previous quarter.
Phishing is a cyberattack that uses malicious email messages, text messages, or voice calls to trick people into sharing sensitive data; downloading malware, visiting malicious websites, and others. Zscaler Threatlabz research shows a nearly 50% increase in Phishing attacks with education, finance, and government being the most targeted.
Spear Phishing
Spear phishing is a highly effective tactic, as these attacks account for over 90% of successful data breaches. This brings the radar to making spear phishing the biggest risk facing businesses worldwide. Spear phishing is targeted phishing that looks like:
- a message sent to a specific individual or group of individuals
- a highly personalized message based on research
- a crafted message that appears to have come from a sender who has a relationship with the recipient
Spear phishing is much rarer than phishing attacks, but they leave a massive impact than bulk phishing scams. With whale phishing and business email comprises becoming the popular spear phishing attacks. It has made the cybercrime landscape more violent.
Most targeted industries by Phishing attacks:
Phishing attacks typically aim at CEOs, CFOs, or similar ranks within an industry or a specific business. Business Compromise Email (BCE) is a scam where a criminal poses as a business partner, customer, or vendor of the target recipient. As per Vade Secure; financial services, cloud, social media, eCommerce, logistics, internet, telco, and government sectors were largely targeted by the phishing attacks in Q3 of this year.
Most targeted industries by Spear Phishing attacks:
The year 2023 saw Microsoft, PayPal, Facebook, and many other giant businesses facing brand abuse by spear phishing attacks. C-level executives, politicians, and celebrities are the top targets of spear phishing attacks worldwide.
What can be done to counter such a surge in cybercrime rates?
Cybersecurity specialists are the cyber genies that work their magic to bring peace to giant business groups that are vulnerable to attacks. They are the shield that must be hired by every business to safeguard their sensitive data and core business information. With cyberattacks growing at an alarming rate, it is critical aspect of an organization to hire quality cyber brigades that can protect their data, money, and brand reputation.
What constitutes a certified cybersecurity specialist?
Although, there is a plethora of skills that can be demanded of you as a cybersecurity expert. However, the ones listed below are deemed high-importance due to their immediate acceptance in an effective role performance.
- Network security control
- Cloud security
- Mobile device management
- Intrusion detection
- Penetration testing
- Operating systems
- Incident response
- DevOps
- Threat knowledge
- Digital forensics
- Programming
- System Administration
This could just be the beginning of what is demanded of a cybersecurity professional. Becoming one needs a great deal of perseverance, skill, and the right certification on board.
Final word:
It is high time the cybersecurity aspirants thought of entering the vast industry with a bang. The time is now to make it happen as the cybercrime rate is at its all-time high and is projected to scale further. Making yourself an indispensable part of a business giant is at the core of a cybersecurity expert’s career. With the best cybersecurity certifications gracing your portfolio; you are sure to settle for the best cybersecurity job roles possible.





