Essential Practices for an Effective Encryption Key Management
Encryption Key Management is a highly advanced technique used in the cybersecurity field for securely generating, storing, distributing, as well as destroying cryptographic keys. Cryptographic keys are secured keys that are used to encrypt and decrypt sensitive data. With the help of effective key management, cybersecurity experts can easily maintain the confidentiality, integrity, and availability of encrypted information.
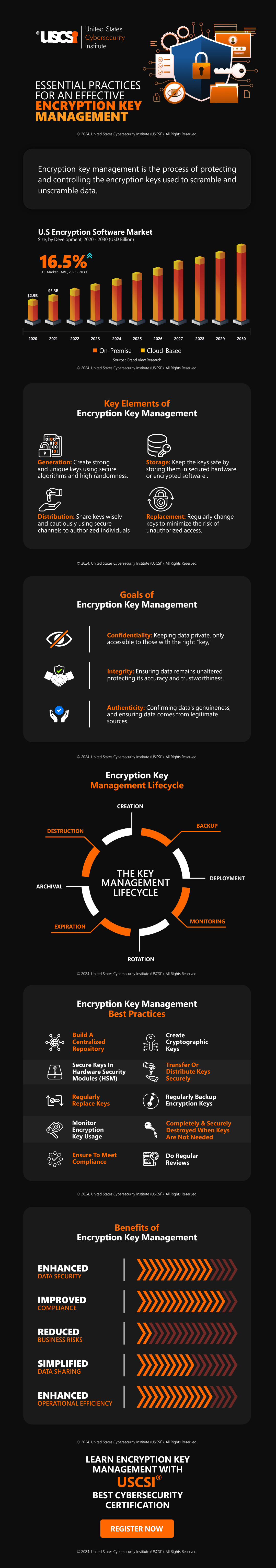
In the past few years, encryption key management has gained huge traction, with several organizations providing services and tools for effective key management. The Encryption software market in the US particularly has seen huge growth and it is expected to grow at a CAGR of 16.5% by 2030.
Effective encryption key management includes several important tasks including key generation using strong cryptographic algorithms, key storage in secure repositories such as Hardware Security Modules (HSMs), key management, distribution, etc.
If you are looking to get into a cybersecurity career then learning this cybersecurity skill is a must for you. You can take advantage of the best cybersecurity certification programs to learn what’s new and trending in these technologies. The infographic below highlights essential practices, tools, and a lot of information related to Encryption Key Management.
Learn the basics of Encryption Key Management, explore the infographic now.