

Cybersecurity Risk Management: Processes and Principles
Organizations understand the impact of cyber-attacks on their business reputation as well as customer trust. Therefore, they leave no stone unturned to ensure the organization as well as their customer data is safe and secure. Cybersecurity risk management is one important step to strengthen an organization’s cybersecurity measures. But what does it include?
Well, in today’s highly interconnected world, cyber crimes are on the rise, and businesses of all sizes are facing continuous implosions of cyber-attacks. According to Cybereason, the global cost of cybercrimes in 2023 was a staggering $8 trillion. Data breaches have become more common than ever and last year the average total cost of a data breach was close to $4.35 million (IBM). These incidents and data breaches can result in devastating consequences and lead to huge financial losses, reputational damage, as well as operational disruption.
So, Cybersecurity risk management is an important process that refers to organizations' proactive management of various kinds of cyber threats to their organization. It includes identification, assessment, and remediation strategies.
Why is Cybersecurity Risk Management important?
Cyber attacks can have huge impacts on organizations. While a data breach can expose its customer’s sensitive information, ransomware attacks can halt the entire business operations. These types of attacks can lead to financial penalties, regulatory fines, loss of consumer trust, downtime within the organization, productivity loss, reputational damage, and other serious consequences.
This is where CSRM plays an important role in helping organizations to proactively manage such risks. Cybersecurity experts use it to identify and address vulnerabilities beforehand and avoid them being exploited. Not just that, CSRM programs can also help organizations recover faster from the loss incurred due to unfortunate cyber incidents.
Moreover, there are certain industries where specific regulations are mandatory to implement necessary security controls to protect sensitive information. With an effective CSRM program organizations can easily comply with necessary regulations.
Core Principles of Cybersecurity Risk Management
At its core, cybersecurity risk management involves the basic principles of risk management in the world of cybersecurity. Risk in simple terms is considered the effect of uncertainty, or it is the capability of something negative to exploit an organization’s vulnerabilities and impact their business goals.
Here are the steps involved in an effective cybersecurity risk management process:
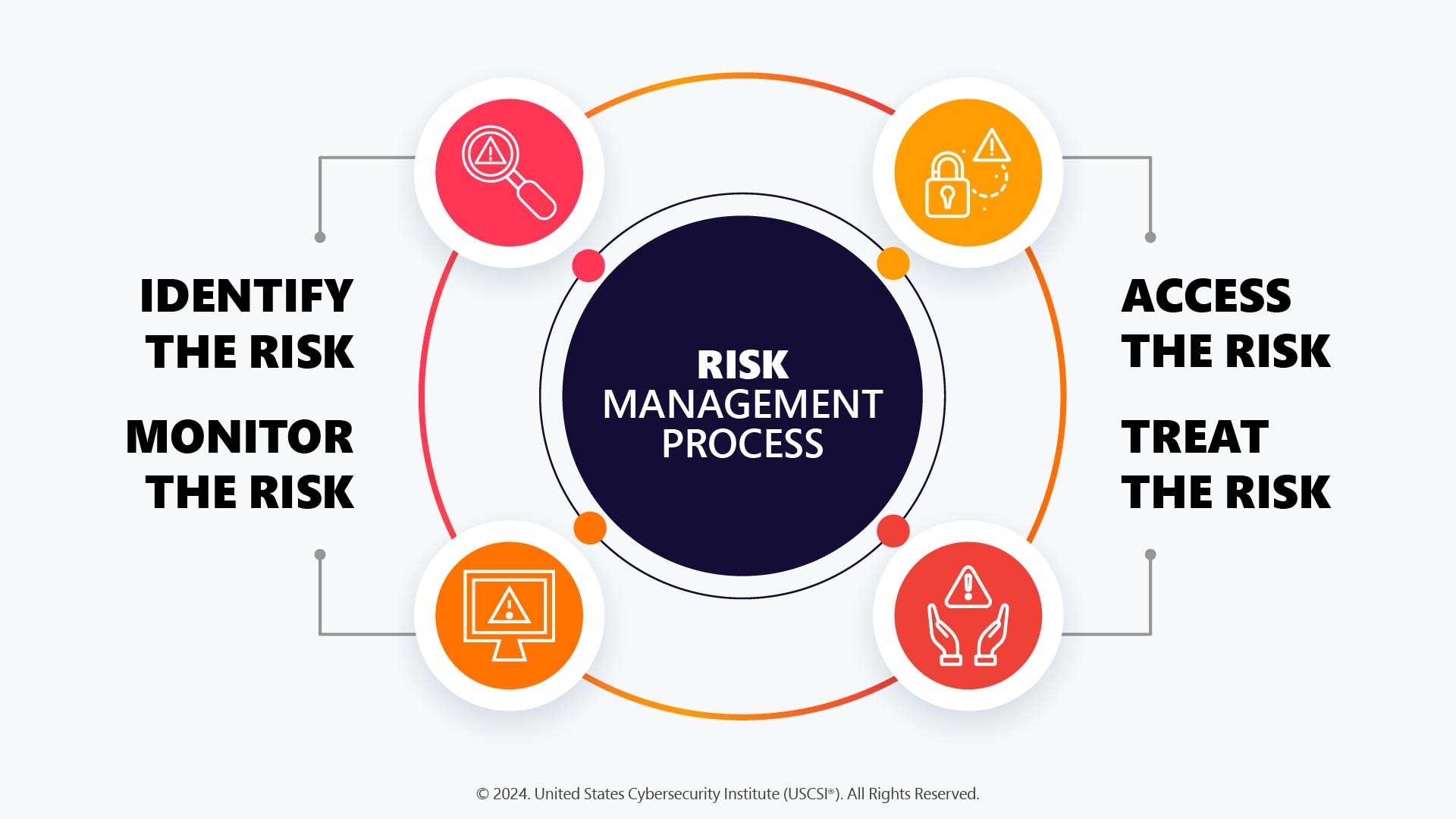
- Identify Risk
This means organizations must understand various threats they can face, what their system or network vulnerabilities can lead to, and what could be their potential consequences
- Assess Risk
After identification, cybersecurity consultants must assess the severity of risks and their potential impacts on the organization’s finances and operations.
- Prioritize Risk
It is important to note that not all risks are important i.e. not all the risks need immediate attention. Therefore, they must rank the risks based on their severity and prioritize which one to address first.
- Mitigate Risk
After ranking the risks on priority, organizations can continue developing strategies like implementing security controls, employee training, or other risk-reduction measures to reduce the impact of cyber threats.
- Monitor Risk
It must also be noted that cybersecurity is an evolving field where new and emerging threats pose even higher risks. So, businesses should continuously monitor the new threats, assess how effective the existing control systems are, and then refine their risk management strategies.
Top cybersecurity certification programs cover the entire cybersecurity risk management process in detail to help students and cybersecurity professionals understand this concept and advance in their cybersecurity careers.
How to implement a robust CSRM?
-
Build a cybersecurity framework
Cybersecurity frameworks provide structure to CSRM that outlines the best practices needed during the identification, assessment, mitigation, and monitoring of risks.
The National Institute of Standards and Technology (NIST) is an important cybersecurity framework that provides a voluntary and customizable approach to cybersecurity. Similarly, ISO 27001 and COBIT 5 are other popular cybersecurity frameworks that can help organizations ensure their CSRM program are complete and include best industry practices.
-
Essential Cybersecurity Controls
Cybersecurity controls refer to the cybersecurity tools and procedures needed to mitigate cybersecurity risks. There are various ways of security controls such as:
- Access control: in this method, the access to systems and data is controlled to give authorization to concerned users only. Multi-factor authorization and role-based access control (RBAC) are popular access control methods.
- Data security: these are control measures that protect data’s confidentiality, integrity, and availability in the organization. this includes data encryption, data backup, recovery, and data classification.
- Network security: in this control method organizations focus on protecting network infrastructure from unauthorized access and malicious activities. Firewalls, IDS, and network segmentation are examples of this control process.
- Incident response: this means having a plan for effective identification, containment, eradication, and recovery from cybersecurity incidents.
-
Employee Training and Awareness
Employees are often the weakest links or most vulnerable in the world of cybersecurity. Therefore, regular training programs are mandatory for organizations to help their employees understand the concepts of cyber threats and how they can protect themselves as well as their organizations from falling victim to different types of evolving cyber threats. Organizations must also consider getting their employees with fundamental cybersecurity certifications for better education on cybersecurity. In such training programs, organizations should cover topics like phishing awareness, social engineering scams, how to set up strong and different passwords for each account and update them regularly, and such other cybersecurity best practices.
Conclusion
Cybersecurity risk management isn’t the final step but an ongoing process that has to continuously evolve with ever-evolving forms of cyber threats. Organizations must continuously monitor their risk profile and update their cybersecurity risk management programs regularly to meet the latest market demands. With the right CSRM program, organizations can significantly reduce the risk of cyber-attacks and protect their important digital infrastructure and sensitive information.





