

A Detailed Overview of Open Cybersecurity Schema Framework (OCSF)
Understanding the cybersecurity trends beforehand is a great fleet that every business expects to succeed and fight against these threats in time. Staying well prepared for the worst cyber threat scenario is the key to a lasting and thriving business panorama. The first quarter of 2024 has witnessed a staggering 28% surge in cyberattacks globally compared to the previous quarter (TOI; quotes Check Point Software Technologies Ltd). Addressing the most urgent need requires businesses to hire cybersecurity professionals who can leverage top-ranking cybersecurity tools worldwide.
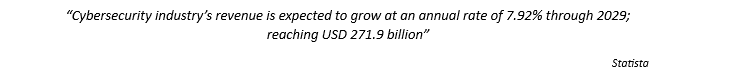
This uptrend is showcasing massively consistent higher bottoms when taking into consideration the global cybersecurity industry revenue growth. Cybersecurity guards are crucial for business health worldwide. Whether yours is a startup or a seasoned business corporation; nobody can evade the risk cybersecurity threats pose nowadays. It is a pressing moment to understand the latest open cybersecurity schema framework; as we combat the world of cyber uncertainties.
Meaning:
The Open Cybersecurity Schema Framework (OCSF) is a collaborative, open-source project delivering a vendor-agnostic, standardized database structure that:
- Normalizes common security event data
- Defines versioning criteria to enable the schema’s evolution
- Lends security log producers and consumers a self-governance process
- Offers security log consumers a vendor-agnostic standardized log structure
The OCSF provides a common platform for highlighting:
- Threat intelligence
- Incident reports
- Indicators of compromise
- Other pertinent cybersecurity information
Target:
There are numerous complex cybersecurity challenges that OCSF strives to resolve. These include:
- Data Silos
The fragmented data hinders the ability to correlate and contextualize threat intelligence across different sources
- Interoperability issues
The scarcity of standardized data formats and schemas makes it difficult for organizations to integrate and interoperate with external threat intelligence feeds and platforms.
- Information overload
The mass volume of cybersecurity data that cybersecurity analysts deal with daily makes it challenging to identify and prioritize cybersecurity threats.
- Inconsistent data quality
Diversities in data formats, semantics, and quality standards undermine the reliability and trustworthiness of threat intelligence. It leads to false positives and missed detections.
To counter these threat scenarios, OCSF is designed to standardize the ways cybersecurity analysts trade and analyze cybersecurity data objects across diverse cybersecurity tools, systems, and organizations.
Components:
3 major components that guide OCSF are:
- TAXONOMY- It is the structure and semantics of cybersecurity data. taxonomy consists of a set of standardized constructs; including
- Observables (IP addresses, domain names, file hashes, URLs)
- Indicators (Signify potential indicators of compromise)
- Incidents (Standardized documentation framework of security breaches, data breaches, and other cybersecurity incidents)
- Bad actors (cybercriminals, cybercriminal organizations, hacktivists, Insider threats)
- Tactics, Techniques, Procedures (TTP) (Methods used by bad actors in cyberattacks)
- DATA TYPES
- String (used to represent textual data, URLs, File paths, etc)
- Numeric (Numerical values such as counts, scores, and timestamps)
- Boolean (represents true or false, binary values)
- Enumeration (predefined set of values, allowing for categorical data representation)
- Array (Collection of values of the same data type)
- Dictionary (Collection of key-value pairs, allowing for more complex data structures)
- ATTRIBUTE DICTIONARY- It provides a standardized set of attributes that can be used to describe cybersecurity data objects. Attributes found in the OCSF attribute dictionary include:
- ID (unique identifier)
- Type (observable, indicator, incident)
- Value (primary value or content of cybersecurity data object)
- Description (descriptive information or context)
- Timestamp (time or date associated with cybersecurity data object)
- Source (origin or source of cybersecurity data object)
- Confidence (level of confidence or certainty associated)
- Tags (additional metadata or labels to categorize or classify cybersecurity data objects)
Format:
The following elements are used to categorize and classify the elements of the data structure:
- Data types, attributes, and arrays
- Event class
- Category
- Profile
- Extensions
OCSF Categories: System activities, findings, identity and access management, network activity, discovery, and application activity
OCSF Event Classes: Caption, Name, ID, Description
OCSF Source Identification: These help in identifying the technology that generated the log or event. The OCSF uses the following values for the VPC Flow Logs from Amazon Web Services (AWS):
- Source: VPC Flow Logs
- Metadata. product.name: Amazon VPC
- Metadata. product. vendor_name: Flowlogs
- Class_name: Network Activity
Personas:
Four major personas in OCSF guide the entire structure of cybersecurity:
- AUTHOR creates and extends the schema using OCSF Github
- PRODUCER generates events natively into the schema; or translates from another schema
- MAPPER translates or creates events from another schema source
- ANALYST or CONSUMER writes rules or analytics against the schema or creates reports from the schema
Benefits:
Growing ahead of the cybersecurity threats is the key when you unravel the core capabilities of Open Cybersecurity Schema Framework (OCSF). Understanding the core beneficial offerings that OCSF lends is massive, and includes:
- Convenient data management
- Smooth correlation of events
- Reduced storage costs
- Data value optimization
In response to the evolving security challenges that the cybersecurity industry faces today; OCSF is a great deal in bringing the cybersecurity threat actors under control. The introduction of a standardized holistic schema assures the delivery of security data consistency, faster analysis, and enhanced collaboration. If you are someone who plans to build a thriving career in cybersecurity; this could be your calling that serves you with the best of career progression opportunities as well as a highly rewarding remuneration structure. Make an informed decision and master these most contemporary and futuristic cybersecurity nuances with the best cybersecurity certification programs worldwide. Explore now to earn big shortly!





