

Quick Guide to Detecting Potential Cyberattacks
No matter how big or small, every organization should have proper strategies and plans in place to identify, detect, and mitigate various kinds of cyber threats looming all around the
They must have a proactive approach plan to protect their network systems, and data from attacks that might include having the IT tools, educating staff regularly, or taking other important steps.
Today, organizations cannot just rely on traditional firewalls and need a multi-layered defense system to thwart attacks before they can cause significant damage. In this article, let us check out some cybersecurity strategies to identify potential cyberattacks even before they occur so that necessary mitigation steps can be taken.
Growing Threat Landscape
The chart below shows the share of cyberattacks across various industries in 2023.
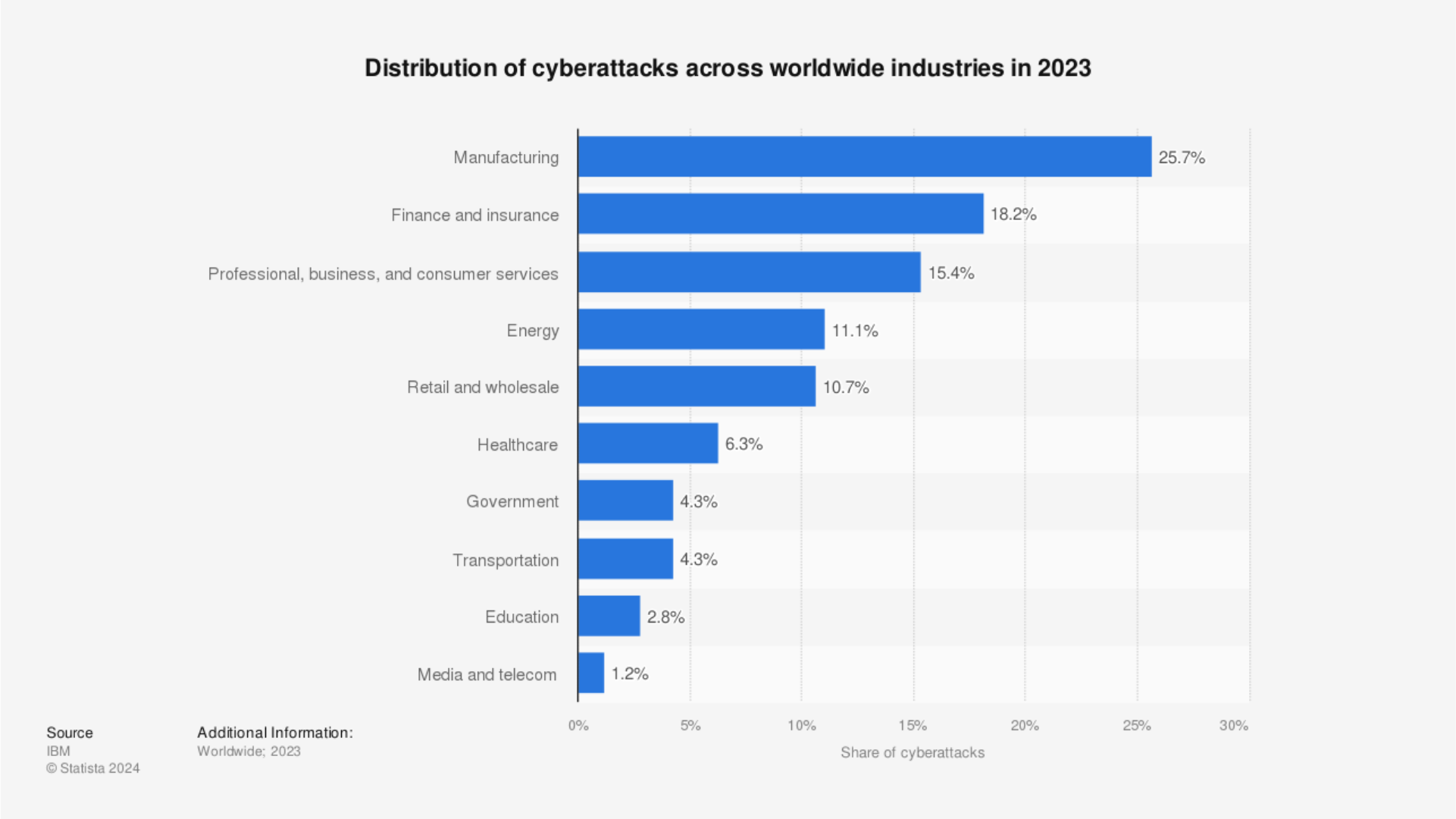
Cyberattacks are a constant threat to organizations. Modern-day businesses are constantly under the radar of cyber criminals and the vulnerabilities can be exploited at any time. According to the Cybersecurity and Infrastructure Security Agency’s 2023 report, businesses encounter an attack every 39 seconds. Not just that the attacks are creating havoc but only in 2023, the cost of cyber-attacks was estimated to be around $8 trillion (IBM).
These numbers highlight the urgent need to implement robust cyberattack detection strategies.
Foundational Cybersecurity Tools
Here are some of the useful and fundamental cybersecurity tools every organization can use as their first line of defense in cybersecurity:
- Network Security Mechanisms
Firewalls are great barriers that filter incoming and outgoing traffic based on predefined security rules. Another important network security tool is SIEM.
- Firewalls: It filters the incoming and outgoing network traffic based on established standard behavior and security regulations. They act as a barrier between trust entities (internal networks) and untrusted external networks (internet).
- Security Information and Event Management (SIEM): SIEM solutions are used to collect, analyze, and correlate log data from various sources within an organization such as its servers, network devices, endpoints, etc. It then helps centralize the monitoring system and facilitates the detection of cyberattacks by analyzing security events in real-time.
- Intrusion Detection System
These are advanced systems used to monitor network traffic and activities. They can identify all kinds of malicious behaviors, monitor network traffic, analyze network packets and detect anomalies or abnormal activities to flag them as potential threats.
- Intrusion Prevention System
Intrusion Prevention Systems not only detect but also help prevent potential cyber threats. They constitute the borderline of network traffic and help filter out malicious network packets and connections per the organization’s established normal standards. IPS is an effective cybersecurity strategy to detect and contain malware, DoS attacks, and other intrusion attempts.
- Endpoint Detection and Response
This technology is used to focus on individual devices aka endpoints within the network. So, organizations can use this EDR solution to monitor endpoint activity and identify if there is any malware, unauthorized access attempts, or any other kinds of malicious behavior. This will help them promptly respond to cyber-attacks in case of an incident.
Advanced Threat Detection Techniques
Apart from using the above-mentioned foundational tools, other advanced cybersecurity techniques offer an even higher level of security:
- Vulnerability Scanning and Penetration Testing
Organizations can use these cybersecurity strategies to identify any kind of vulnerabilities available in their networks and devices. Penetration testing uses advanced ethical hacking practices to identify weaknesses in an organization before they can be exploited. Similarly, vulnerability scanners can also automatically detect vulnerabilities and penetration testing simulates real-world attacks to identify exploitable weaknesses.
- Anomaly Detection
Anomaly detection refers to the technique of identifying if the activities or behaviors are deviating from normal system behavior. This is done by analyzing historical data to flag unusual activities indicating potential attacks.
- Honeypots
Honeypots refers to the decoy systems that are designed to lure attackers. They appear to be legitimate targets but do not contain any real data. After monitoring activities on honeypots, security teams can gain valuable insights into attacker tactics and techniques.
- Threat Intelligence
This refers to staying informed about the different kinds of latest cyber threats that can have a greater impact on organizations. It is the process of gathering information about current attack methods and tactics used by cybercriminals and analyzing them to proactively develop efficient mitigation strategies.
- User and Entity Behavior Analytics (UEBA)
UEBA is used to analyze user and system behaviors to identify anomalies that can indicate potential attacks. In this cybersecurity technique, organizations establish a baseline profile for users and devices and detect if there are any deviations from these established norms. UEBA is an excellent method to detect unusual login attempts, unauthorized data access, or sudden surges in network activity,
- Machine Learning and Artificial Intelligence
Artificial intelligence technology has become highly advanced and has also been deeply integrated into the cybersecurity domain. So, AI and ML can be used to analyze vast amounts of data in real-time and identify hidden patterns and anomalies that can indicate a cyber-attack. AI and ML are also highly efficient in detecting zero-day attacks which are previously unknown vulnerabilities.
Role of Human Expertise
Though the above technologies are highly efficient in detecting and mitigating cyber threats, human vigilance will always be important. Here are some important things to consider:
- Security Awareness Training
Organizations should regularly conduct educational programs for their employees to educate them about cyber threats and best practices. This can cover topics like phishing emails, social engineering tactics, password hygiene, etc. Offering them basic cybersecurity certifications can
alsobe highly beneficial. - Incident Response Planning
Organizations should also have a well-defined plan to respond to various cyber-attacks and contain the damage. This includes defining clear roles and responsibilities for all involved participants.
- Backing up regularly
By regularly backing up organizational data, organizations can protect themselves in case of any unavoidable incidents. However, the backup should be stored securely and isolated from the main network.
Conclusion
Detecting cyber-attacks is difficult but not impossible. It requires a multi-layered approach combining technology and human expertise. So, by implementing the right cybersecurity strategies as discussed in this article, organizations can significantly improve their overall security posture and thwart potential attacks before they can cause huge damage.
Organizations must also understand that cybersecurity is an ongoing process and requires continuous monitoring, adaptation, and awareness. If they are vigilant and proactive, they can build highly efficient defenses against the ever-evolving threat landscape.





