

FishXProxy Phishing Toolkit: A New Threat To Be Aware of
Phishing attacks are the most common form of cyber-attacks. About 41% of all cybersecurity incidents are initiated using phishing attacks. Now, with the release of FishXProxy, phishing attacks will be more powerful, democratized, and will be more in number.
Before we dive deep into what FishXProxy is and why it is a serious concern for the modern digital landscape, we must understand that the world of cybercrime is evolving. Parallel to our safe and secure digital space, where we spend most of our time connecting socially, shopping online, and transacting huge amounts, a dark web exists.
This dark web serves as a marketplace where it hosts a MaaS (Malware-as-a-service) platform for cybercriminals where they can get access to various kinds of cybersecurity tools to help them carry out their attacks.
There are numerous phishing kits available on the dark web and this latest launch is exceptionally capable of breaching all kinds of traditional security measures and defenses to steal user data with a very high success rate.
As mentioned above, phishing attacks are the most prevalent attacks, and the graph below shows how it has impacted various industries.
Online industries worldwide most targeted by phishing attacks as of 1st quarter 2024
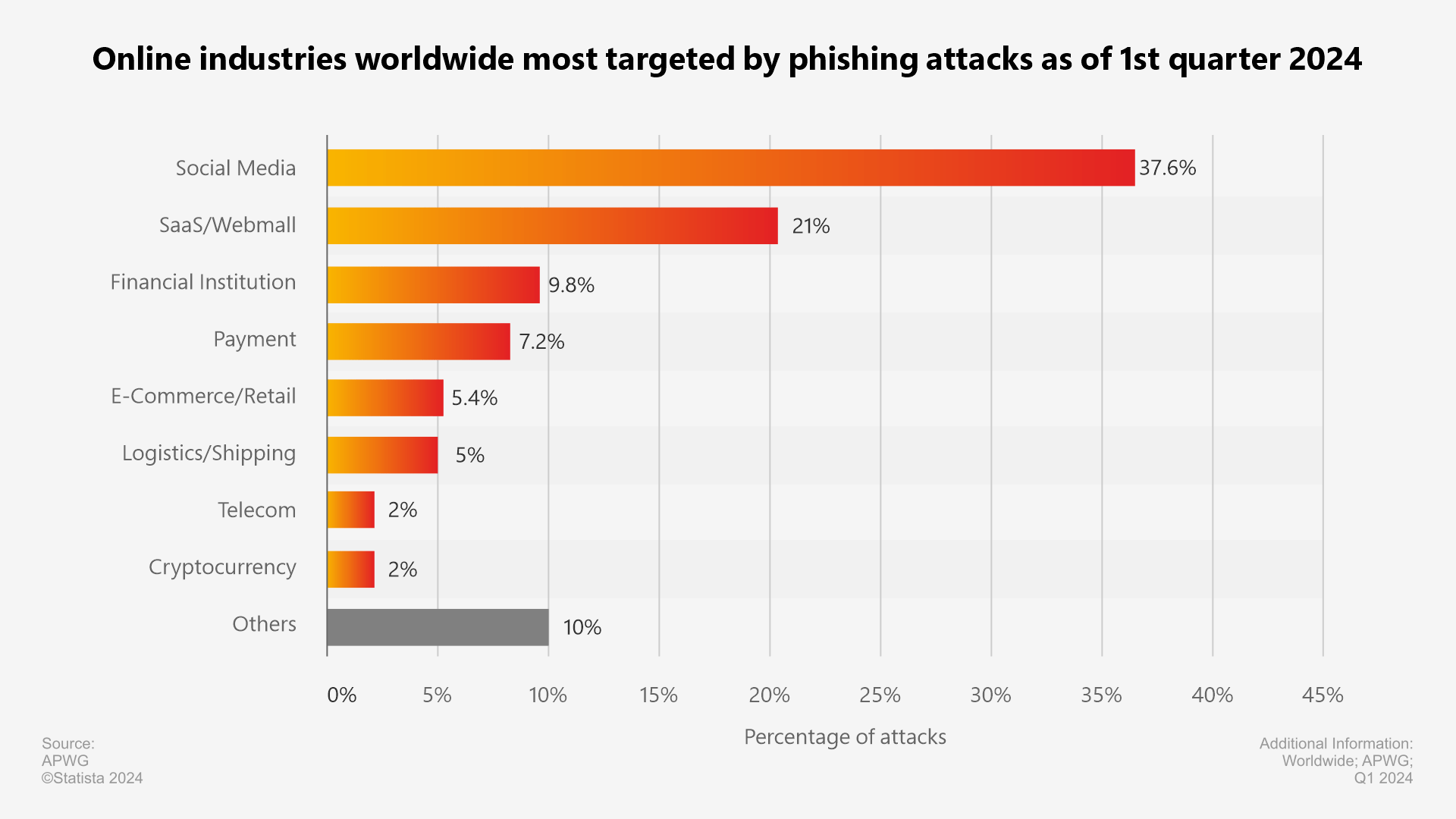
And with FishXProxy in access, almost all industries will face this serious issue now.
Callie Guenther, a senior manager of cyber threat research at Critical Start says that the release of the FishXProxy phishing kit highlights how far the modern threat landscape has come and how advanced technologies are available to develop attack tools that are hard to detect and prevent by traditional security defenses. She adds this democratization of highly advanced cybersecurity tools will encourage even non-technical attackers to effectively launch phishing campaigns with a high success rate.
FishXProxy is marketed on the dark web as “The Ultimate Powerful Phishing Toolkit” which is capable of reducing the entry barrier for cybercriminals to conduct phishing attacks at a large scale.
Therefore, we expect a significant rise in the volume and sophistication of upcoming phishing attacks. Organizations must also acknowledge that it is the need of the hour to develop more advanced and multi-layered security solutions to protect users and data from evolving phishing attacks.
Understanding FishXProxy in Detail
By now we understand that it is a comprehensive phishing toolkit that makes it easier to launch sophisticated attacks with ease. Here are some of the features of this tool that make it possible.
- Easy integration with Cloudflare
FishXProxy can leverage Cloudflare’s infrastructure and use its enhanced performance, security, and legitimacy. As it is integrated with Cloudflare, traditional security solutions cannot detect or block phishing sites.
- Dynamic content generation
Using this phishing toolkit, attackers can create highly personalized phishing pages mimicking genuine websites and help them gain user trust.
- Anti-bot measures
FishXProxy also has some anti-bot mechanisms such as Cloudflare’s CAPTCHA that can bypass automated detection and analysis of phishing campaigns.
- Cross-Project Tracking
This feature of FishXProxy helps the attackers monitor and track the users across various phishing campaigns so that they can create even more realistic profiles and develop future attacks accordingly.
- Page Expiration
Page expiration refers to the short lifespan of phishing pages that disappear when their job is done. This makes it difficult for cybersecurity professionals to analyze or respond to these threats promptly.
What is its impact on victims?
The launch of FishXProxy has significantly increased the number of phishing attacks. Since it has a very user-friendly interface and powerful features, it has become a popular choice among criminals. With its high success rate, it has started affecting users in all fields including businesses, individuals, and government. Phishing attacks steal personal information, financial data, credentials, and other important sensitive information that leads to financial loss, identity theft, reputational damage, and much more. The stealing of confidential information also disrupts normal business operations.
How to protect from advanced phishing attacks?
Even though FishXProxy offers a highly advanced phishing toolkit for attackers, we can protect ourselves from innovative and sophisticated phishing attacks by following some simple steps.
- Employee education
Organizations must conduct regular awareness programs about phishing tactics and should be trained to recognize the signs of phishing emails. They can offer cybersecurity certifications to enhance their cybersecurity skills and identify and prevent phishing attacks easily.
- Strong passwords
Every platform should also incorporate a complex password policy. Users can also use system password generators that are difficult to crack.
- Updated security software
To combat advanced attack tactics, it is necessary to use the latest and even more advanced security solutions. So, always use the latest software and update your software with the latest security patches.
- Email Filtering
Use the built-in email filter features of the email service provider to block suspicious phishing emails and attachments.
- Never click suspicious links
Always avoid clicking links on emails or downloading attachments from emails that look suspicious.
Following these steps, you can protect yourself and your organization from heavy losses.
Conclusion
The world of cybercrimes is constantly evolving and growing. FishXProxy proves this statement as it is among the most advanced toolkits enabling attackers to carry out sophisticated attacks at much ease and on a larger scale. Its easy accessibility, user-friendly features, and powerful tools allow even non-technical attackers to carry out phishing attacks at higher success rates. However, by using proactive measures as mentioned in this article, users and organizations can minimize the impact and keep their data and assets safe.





