

Cybersecurity Mesh Architecture (CSMA): An Overview
The digital infrastructure of modern-day businesses isn’t limited to local servers, desk devices, and simple internet connection. Organizations these days are actively adopting cloud infrastructure, remote workforces, and the use of numerous interconnected IoT devices that can make work easier and more productive. And this expanded horizon of the digital landscape has also increased the security perimeter for which traditional cybersecurity strategies might prove to be ineffective.
These factors are some of the major reasons why organizations are struggling to protect their digital infrastructure against evolving cyber-attacks. The centralized security systems are proving to be ineffective. However, Cybersecurity Mesh Architecture is one important element of cybersecurity widely used to address these challenges.
Security Silos and Growing Complexity
The traditional security systems were mostly focused on the security of well-defined network security boundaries. Organizations use firewalls and intrusion detection systems (IDS) as the first line of defense that protects their internal resources.
However, with the rise in the adoption of cloud technologies, and mobile and IoT devices, the security perimeter has expanded rapidly as well as become porous. Organization’s valuable data and applications are located at remote places spread across the world that need to be accessed from any other corner of the world. This distributed environment presents some significant cybersecurity challenges that need to be addressed such as:
- Security silos
Organizations have to deploy patchwork of security tools from different vendors which obviously operate independently and create blind spots leading to ineffective communication. ISC2 in its Cybersecurity Workforce Report 2023 mentioned 64% of organizations struggle with siloed security tools. This is a huge obstacle in detecting and responding to threats.
- Increased Attack Surface
Secondly, the number of interconnected devices is on the rise. This has increased the overall attack surface for the attackers where each device can serve as an excellent entry point for them. A 2024 Gartner report predicted by 2030, the world will have around 43 billion connected devices. So, we can imagine the huge attack surface the cyber criminals may enjoy.
- Inefficient security operations
Lastly, managing several security tools located across the world can be a difficult task for cybersecurity professionals who have to continuously monitor, configure, and correlate logs. This can be resource resource-intensive process.
These factors led to the need for a robust solution – Cybersecurity Mesh Architecture.
What is Cybersecurity Mesh Architecture? – The Perfect Solution
The Cybersecurity Mesh Strategy was introduced by Gartner and it serves as an efficient security system in today’s highly dynamic IT landscape. This security model is composable and scalable and takes advantage of interoperable security tools that work together as a unified fabric. Cybersecurity mesh applications work entirely differently from traditional architectures. They break down security silos and help with seamless communication and information sharing between different components.
Here is how CSMA works:
There are several interconnected security tools making a dynamic web and each of them is specialized in a specific area such as endpoint security, cloud security, identity management, and so on. These tools then connect with a central security mesh platform where they share intelligence and coordinate responses.
Enroll in top cybersecurity courses and cybersecurity certification programs to learn in-depth about implementing cybersecurity mesh strategy and enhancing organizations' overall network security.
Benefits of Cybersecurity Mesh Architecture
Through this coordinated and collaborative approach, they help organizations reap several benefits like:
- Better Security Posture
As they ensure a culture of collaboration and information sharing, cybersecurity mesh architecture helps to make the security system more efficient. Cybersecurity professionals and security teams can detect threats faster and respond more effectively. This helps organizations to minimize the impact of security incidents.
- Improved Agility and Scalability
As cybersecurity mesh applications offer a modular approach, organizations can easily integrate new security tools as and when needed. With this flexibility, they can easily adapt to new and emerging kinds of cyber threats and technological advancements.
- Reduces complex security systems and cost
CSMA is a centralized security management solution and thus helps to streamline various security operations. This further leads to cost savings as it minimizes redundancy and simplifies the overall security tool management process.
As per a study by Cybersecurity Insiders 2023, organizations that use consolidated security platforms were able to reduce security spending by 12%.
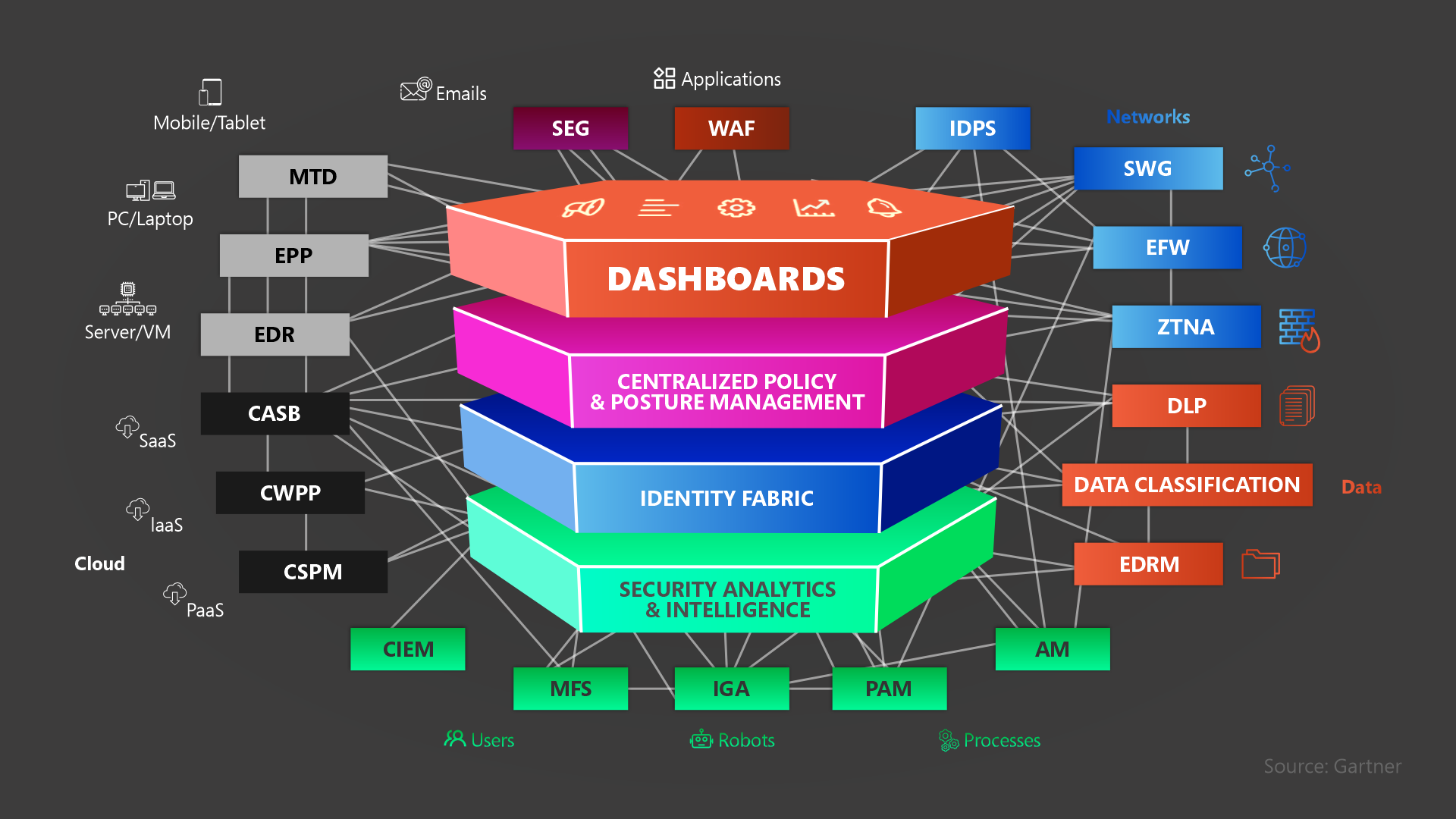
Components of Cybersecurity Mesh Architecture
There are 4 layers of cybersecurity mesh architecture:
- Consolidated Policy and Posture Management: Enforces consistent security policies across all devices and environments.
- Security Analytics and Intelligence: Collects security from various sources to help with efficient threat detection and analysis.
- Distributed Identity Fabric: CSMA’s unified identity management system helps to simplify access control and reduces the attack surface. It then helps organizations to prevent unauthorized access and the risks associated with it.
- Consolidated Dashboards: It provides organizations with a clear view of their security posture. This centralized view enhances security controls, and incident response much faster.
Conclusion
Cybersecurity Mesh Architecture (CSMA) is the latest way to control an organization’s overall security posture spread across countries, devices, and networks from a centralized place. It helps to break down security silos, enhances communication and collaboration, and offers composable and scalable architecture. Thus, it helps organizations to improve their overall security posture for their ever-expanding digital landscape.





